Technology

- DID
- Cryptography
- Smart contract
- Cross Chain
- TPS
Organization
Exchange
Digital assets
CBDC
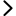
Dapp
Network
Decentralized Identity: Passport to Web3

Introduction
The internet was created without a native identity layer for people. Because of this, the issue of digital identity was relegated to websites and applications. This siloed approach may have been appropriate for the early days of the internet, but with billions of people now online, its drawbacks are becoming more apparent. Usernames and passwords continue to be the dominant paradigm, despite being repeatedly demonstrated to be an insecure model. The average person has to juggle between 70 to 80 passwords, resulting in a decidedly inferior user experience. Indeed, there are multi-million dollar businesses built just around helping businesses and individuals manage their fragmented accounts, such as Okta, 1Password, and Dashlane. Most importantly, users do not actually own their online identity. Instead, they rent it from companies and centralized entities. Thus, they are prone to the risk of their digital identity being hacked, manipulated, censored, or simply lost.
The emergence of Web3, which fundamentally embeds economic transfers, has brought about a renewed emphasis on creating robust identity systems. Although decentralized identity (DID) has been a largely overlooked topic compared to DeFi, NFTs, and DAOs, we view it as a critical technological primitive that enables native Web3 applications. If we create a shared, flexible, and resilient identity layer, we can drastically unlock the pace of innovation by creating a wider design space.
In this report, we introduce key DID concepts and the current DID ecosystem on a high level and dive deeper into select projects that are at the forefront of building the identity foundation of Web3.
Decentralized Identity (DID)
The DID specification from the W3C is the widely-accepted standard, ensuring that identity systems can interoperate across different networks and platforms.
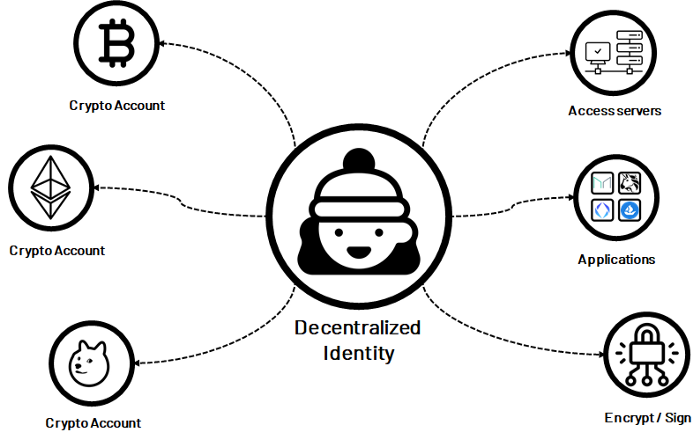
An overview of the DID architecture is illustrated below. A DID is an address on the internet that someone can own and control directly. It can be used to find connected DID documents, which contain information associated with the DID. DID documents contain relevant information to enable use cases, such as sign-in, data encryption, communication, etc. Cryptographic proofs, such as digital signatures, allow entities to prove control over these identifiers.
Basic Components of DID Architecture
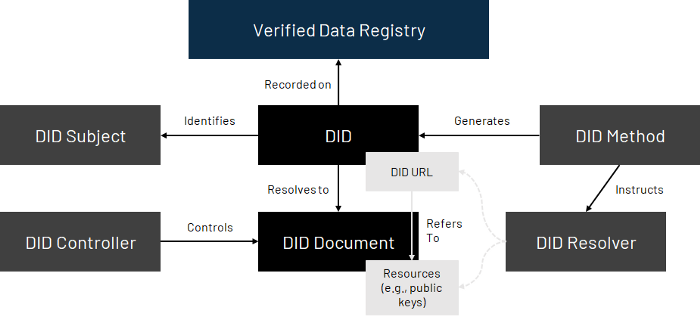
In sum, the DID serves as the identity hub. Because users control their hub, they can decide when, with whom, and under what terms they reveal elements of their digital identity. And with greater adoption of the DID standard, individuals are not locked into a single ecosystem or siloed approach.
DIDs Provide Users with Control, Security, Privacy, and Portability
DIDs Enabling New Use Cases
In the physical world, identity is integral to a well-functioning society. Passports enable governments to identify their citizens, driver’s licenses allow citizens to claim rights to the road, university degrees confer qualifications, etc.
Similarly, DIDs will enable high-value internet economic activity. Below, we highlight some current Web3 pain points that DIDs could solve.
NFTs — Authenticity and Identity
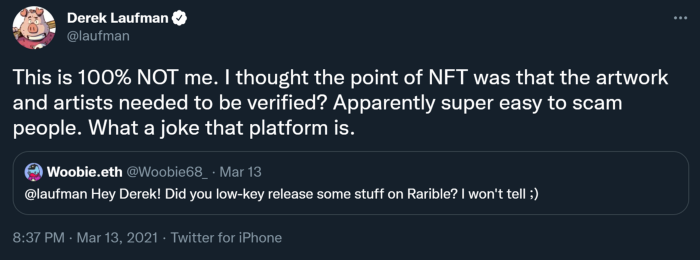
Fraud and copyminting continue to plague artists and creators. For instance, Derek Laufman, a digital artist and designer of Marvel’s Super Hero Adventures, saw his works being auctioned off on NFT platform Rarible without his knowledge. Similar stories like this are common.
NFT Fraud Continues to Plague Artists
A strong DID infrastructure solves this. Applications can build off of DID to allow creators to provably sign off that an NFT, representing a digital or physical asset, was created by them. Buyers and sellers will be able to verify the provenance of the digital artwork too. DIDs could also help foster greater engagement between artists and their community, such as restricting NFT ownership to community members to limit speculation from scalpers or serving exclusive NFT content to select holders.
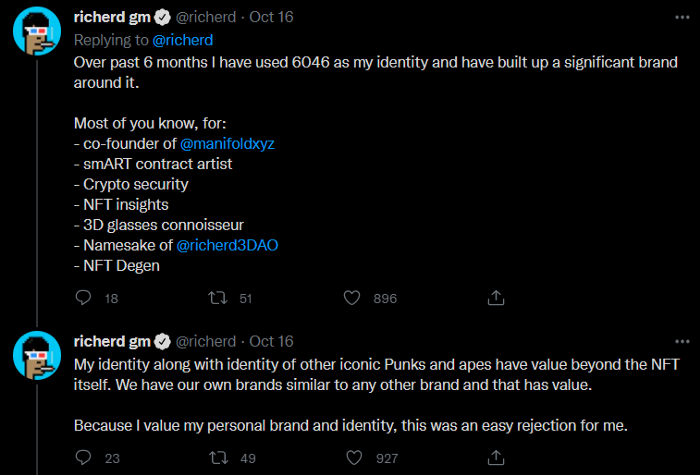
More broadly, NFTs could serve as one anchor for decentralized identity. Already, several users identify their online presence not merely with a username but also with an NFT project. As an example, co-founder of Manifold @richerd explained that he turned down a $9.5 million offer for his cryptopunk NFT because he identifies his cryptopunk as his identity and brand.
NFTs As Online Identities
Unlocking the Next Phase of DeFi
Collateralized loans have served as the backbone of DeFi growth so far. But because crypto finance protocols aim to be fully trustless and permissionless, they often required over-collateralization. For instance, loans taken out on ETH on MakerDAO require collateralization ratios of 130–170%. This has powered DeFi growth over the last year, but the collateral requirements restrict the use cases to mostly crypto traders looking to take on leverage. For most people, the reason they want to borrow is that they do not already have the money that they need.
Lowering or completely removing the collateral requirement is key to introducing DeFi to mass adoption. Having a strong DID layer could allow for “on-chain” credit scores, providing users access to credit-based lending. Furthermore, because users directly control their credit score, they can better monitor and adjust their borrowing/lending behavior. Thus, DID offers the chance of further democratizing decentralized financial systems.
In addition, having a strong identity layer to financial applications could solve other current problems in DeFi, such as:
- Improving fair distribution of token airdrops by authenticating actual members and reducing the potential for bots to dilute airdrop events.
- Using DIDs to gate access to DeFi pools to reduce spam/sybil attacks or enable institutions to participate by providing compliance tools to identify counterparties.
- Guiding users through the dark forest of Ethereum by illuminating participants that can be trusted act in positive-sum ways.
Decentralized Autonomous Organizations (DAOs)
DAOs often use token-based governance for voting, influence, and priorities. This generally makes sense — large tokenholders have the most skin-in-the-game — but it can exclude or deprioritize active contributors who may not have large amounts of capital. And although members can build their reputation within a DAO, they may need to build credibility from scratch in a new context.
DIDs could preserve a user’s reputation across multiple DAOs. Porting over credentials from one DAO to another reflects the reputation portability that we already enjoy in the physical world, preventing active contributors from having to start from zero. Furthermore, other Web3 contexts, such as participation in Gitcoin, publications to Mirror, or code contribution to Radicle, could further help DAOs find qualified candidates.
The DID Ecosystem
The DID ecosystem can be broken down into layers, in which each layer on the top builds upon the underlying protocol. We leverage and slightly modify DIF’s 4-Layer Identity Model to map current DID projects by their primary focus, with the caveat that this is a simplifying model and most projects transcend one layer.
The Decentralized Identity Ecosystem by Layers
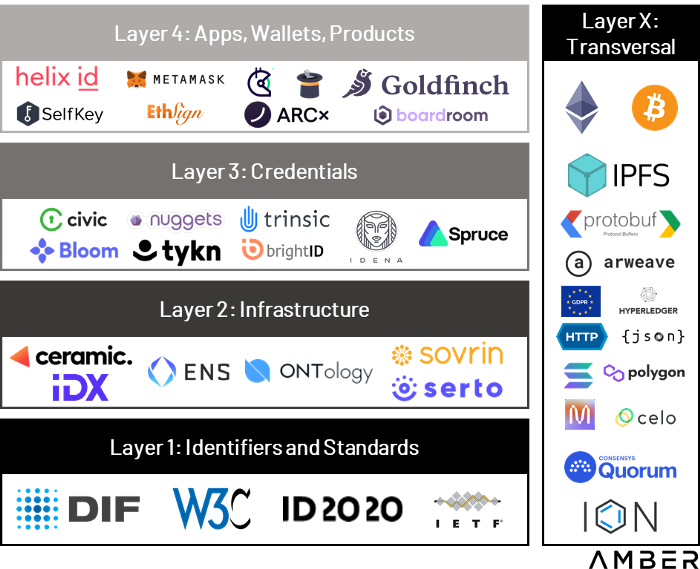
Layer 1: Identifiers and Standards
Standards, identifiers, and namespaces create the public trust layer, ensuring standardization, portability, and interoperability. They also allow networks to register and govern DID methods, providing developers and users with the rules and context of the network’s ID system.
The Decentralized Identity Foundation (DIF) is the key player of this layer and the cornerstone of the ecosystem. It acts as the center for development, discussion, and management of all activities required to create and maintain an interoperable & open ecosystem for the DID stack.
Layer 2: Infrastructure
Infrastructure and agent frameworks allow applications to interact directly with each other and verifiable data registries. These solutions include communication, storage, and key management. We highlight Ceramic and ENS as projects at the front line of building DID infrastructure (although ENS’ categorization can be debated, we place it at the infrastructure layer as we foresee credentials and applications will be built on top of ENS in the future).
Layer 3 : Credentials
Credentials have to be managed, updated, and exchanged. This layer aims to address how DIDs can negotiate proof of control and authentication, as well as securely passing data between identity owners.
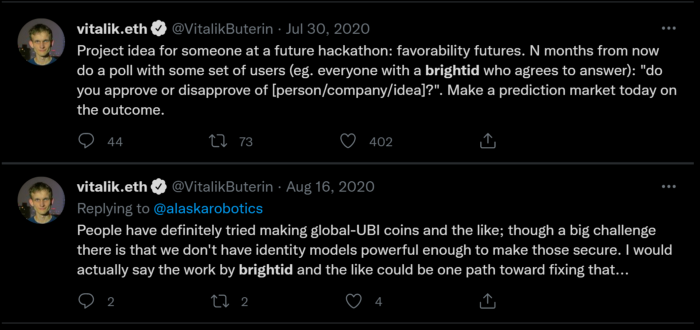
BrightID is a notable project in this area. It is a social identity network with over 30,000 users that allows people to prove to applications that they aren’t using multiple accounts, thus minimizing the chances of sybil attacks.
Vitalik Buterin on BrightID’s Potential Applications
Layer 4: Apps, Wallets, and Products
This layer is likely most familiar to readers and intends to provide real-world use cases and value to consumers. Some projects, such as Goldfinch (uncollateralized lending), use proprietary unique entity checks but aim to leverage decentralized ID solutions when they mature. In contrast, other applications already leverage existing DID technologies, such as TrueFi (uncollateralized lending with on-chain credit scores), Gitcoin (funding of public goods), and Ethsign (decentralized electronic agreements).
Layer X: Transversal
These projects largely transcend any individual layer and have consequences at multiple levels. For instance, Europe’s GDPR data protection law has ramifications across all areas of the ecosystem.
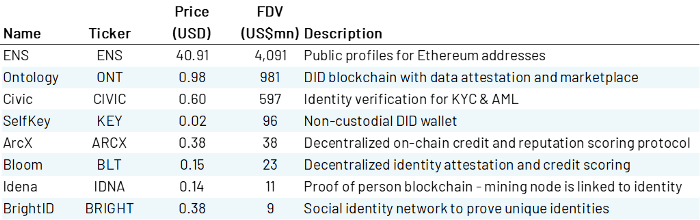
Token Valuations in the DID Ecosystem
References
Decentralized Identity: Passport to Web3,Amber Group,Nov 23, 2021Cryptography
Cryptography, or cryptology (from Ancient Greek: κρυπτός, romanized: kryptós "hidden, secret"; and γράφειν graphein, "to write", or -λογία -logia, "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, electrical engineering, communication science, and physics. Applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications.
Cryptography prior to the modern age was effectively synonymous with encryption, converting information from a readable state to unintelligible nonsense. The sender of an encrypted message shares the decoding technique only with intended recipients to preclude access from adversaries. The cryptography literature often uses the names Alice ("A") for the sender, Bob ("B") for the intended recipient, and Eve ("eavesdropper") for the adversary. Since the development of rotor cipher machines in World War I and the advent of computers in World War II, cryptography methods have become increasingly complex and its applications more varied.
Modern cryptography is heavily based on mathematical theory and computer science practice; cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in actual practice by any adversary. While it is theoretically possible to break into a well-designed system, it is infeasible in actual practice to do so. Such schemes, if well designed, are therefore termed "computationally secure"; theoretical advances (e.g., improvements in integer factorization algorithms) and faster computing technology require these designs to be continually reevaluated, and if necessary, adapted. Information-theoretically secure schemes that provably cannot be broken even with unlimited computing power, such as the one-time pad, are much more difficult to use in practice than the best theoretically breakable, but computationally secure, schemes.
The growth of cryptographic technology has raised a number of legal issues in the Information Age. Cryptography's potential for use as a tool for espionage and sedition has led many governments to classify it as a weapon and to limit or even prohibit its use and export. In some jurisdictions where the use of cryptography is legal, laws permit investigators to compel the disclosure of encryption keys for documents relevant to an investigation. Cryptography also plays a major role in digital rights management and copyright infringement disputes in regard to digital media.
Terminology
The first use of the term "cryptograph" (as opposed to "cryptogram") dates back to the 19th century—originating from "The Gold-Bug," a story by Edgar Allan Poe.
Until modern times, cryptography referred almost exclusively to "encryption", which is the process of converting ordinary information (called plaintext) into unintelligible form (called ciphertext). Decryption is the reverse, in other words, moving from the unintelligible ciphertext back to plaintext. A cipher (or cypher) is a pair of algorithms that carry out the encryption and the reversing decryption. The detailed operation of a cipher is controlled both by the algorithm and, in each instance, by a "key". The key is a secret (ideally known only to the communicants), usually a string of characters (ideally short so it can be remembered by the user), which is needed to decrypt the ciphertext. In formal mathematical terms, a "cryptosystem" is the ordered list of elements of finite possible plaintexts, finite possible cyphertexts, finite possible keys, and the encryption and decryption algorithms which correspond to each key. Keys are important both formally and in actual practice, as ciphers without variable keys can be trivially broken with only the knowledge of the cipher used and are therefore useless (or even counter-productive) for most purposes. Historically, ciphers were often used directly for encryption or decryption without additional procedures such as authentication or integrity checks.
There are two main types of cryptosystems: symmetric and asymmetric. In symmetric systems, the only ones known until the 1970s, the same secret key encrypts and decrypts a message. Data manipulation in symmetric systems is significantly faster than in asymetric systems. Asymmetric systems use a "public key" to encrypt a message and a related "private key" to decrypt it. The advantage of asymmetric systems is that the public key can be freely published, allowing parties to establish secure communication without having a shared secret key. In practice, asymmetric systems are used to first exchange a secret key, and then secure communication proceeds via a more efficient symmetric system using that key. Examples of asymmetric systems include Diffie–Hellman key exchange, RSA (Rivest–Shamir–Adleman), ECC (Elliptic Curve Cryptography), and Post-quantum cryptography. Secure symmetric algorithms include the commonly used AES (Advanced Encryption Standard) which replaced the older DES (Data Encryption Standard). Insecure symmetric algorithms include children's language tangling schemes such as Pig Latin or other cant, and all historical cryptographic schemes, however seriously intended, prior to the invention of the one-time pad early in the 20th century.
In colloquial use, the term "code" is often used to mean any method of encryption or concealment of meaning. However, in cryptography, code has a more specific meaning: the replacement of a unit of plaintext (i.e., a meaningful word or phrase) with a code word (for example, "wallaby" replaces "attack at dawn"). A cypher, in contrast, is a scheme for changing or substituting an element below such a level (a letter, or a syllable or a pair of letters, etc.) in order to produce a cyphertext.
Cryptanalysis is the term used for the study of methods for obtaining the meaning of encrypted information without access to the key normally required to do so; i.e., it is the study of how to "crack" encryption algorithms or their implementations.
Some use the terms "cryptography" and "cryptology" interchangeably in English, while others (including US military practice generally) use "cryptography" to refer specifically to the use and practice of cryptographic techniques and "cryptology" to refer to the combined study of cryptography and cryptanalysis. English is more flexible than several other languages in which "cryptology" (done by cryptologists) is always used in the second sense above. RFC 2828 advises that steganography is sometimes included in cryptology.
The study of characteristics of languages that have some application in cryptography or cryptology (e.g. frequency data, letter combinations, universal patterns, etc.) is called cryptolinguistics.
History of cryptography and cryptanalysis
Before the modern era, cryptography focused on message confidentiality (i.e., encryption)—conversion of messages from a comprehensible form into an incomprehensible one and back again at the other end, rendering it unreadable by interceptors or eavesdroppers without secret knowledge (namely the key needed for decryption of that message). Encryption attempted to ensure secrecy in communications, such as those of spies, military leaders, and diplomats. In recent decades, the field has expanded beyond confidentiality concerns to include techniques for message integrity checking, sender/receiver identity authentication, digital signatures, interactive proofs and secure computation, among others.
Classic cryptography
The main classical cipher types are transposition ciphers, which rearrange the order of letters in a message (e.g., 'hello world' becomes 'ehlol owrdl' in a trivially simple rearrangement scheme), and substitution ciphers, which systematically replace letters or groups of letters with other letters or groups of letters (e.g., 'fly at once' becomes 'gmz bu podf' by replacing each letter with the one following it in the Latin alphabet). Simple versions of either have never offered much confidentiality from enterprising opponents. An early substitution cipher was the Caesar cipher, in which each letter in the plaintext was replaced by a letter some fixed number of positions further down the alphabet. Suetonius reports that Julius Caesar used it with a shift of three to communicate with his generals. Atbash is an example of an early Hebrew cipher. The earliest known use of cryptography is some carved ciphertext on stone in Egypt (ca 1900 BCE), but this may have been done for the amusement of literate observers rather than as a way of concealing information.
The Greeks of Classical times are said to have known of ciphers (e.g., the scytale transposition cipher claimed to have been used by the Spartan military). Steganography (i.e., hiding even the existence of a message so as to keep it confidential) was also first developed in ancient times. An early example, from Herodotus, was a message tattooed on a slave's shaved head and concealed under the regrown hair. More modern examples of steganography include the use of invisible ink, microdots, and digital watermarks to conceal information.
In India, the 2000-year-old Kamasutra of Vātsyāyana speaks of two different kinds of ciphers called Kautiliyam and Mulavediya. In the Kautiliyam, the cipher letter substitutions are based on phonetic relations, such as vowels becoming consonants. In the Mulavediya, the cipher alphabet consists of pairing letters and using the reciprocal ones.
In Sassanid Persia, there were two secret scripts, according to the Muslim author Ibn al-Nadim: the šāh-dabīrīya (literally "King's script") which was used for official correspondence, and the rāz-saharīya which was used to communicate secret messages with other countries.
David Kahn notes in The Codebreakers that modern cryptology originated among the Arabs, the first people to systematically document cryptanalytic methods. Al-Khalil (717–786) wrote the Book of Cryptographic Messages, which contains the first use of permutations and combinations to list all possible Arabic words with and without vowels.
Ciphertexts produced by a classical cipher (and some modern ciphers) will reveal statistical information about the plaintext, and that information can often be used to break the cipher. After the discovery of frequency analysis, perhaps by the Arab mathematician and polymath Al-Kindi (also known as Alkindus) in the 9th century, nearly all such ciphers could be broken by an informed attacker. Such classical ciphers still enjoy popularity today, though mostly as puzzles (see cryptogram). Al-Kindi wrote a book on cryptography entitled Risalah fi Istikhraj al-Mu'amma (Manuscript for the Deciphering Cryptographic Messages), which described the first known use of frequency analysis cryptanalysis techniques.
Language letter frequencies may offer little help for some extended historical encryption techniques such as homophonic cipher that tend to flatten the frequency distribution. For those ciphers, language letter group (or n-gram) frequencies may provide an attack.
Essentially all ciphers remained vulnerable to cryptanalysis using the frequency analysis technique until the development of the polyalphabetic cipher, most clearly by Leon Battista Alberti around the year 1467, though there is some indication that it was already known to Al-Kindi. Alberti's innovation was to use different ciphers (i.e., substitution alphabets) for various parts of a message (perhaps for each successive plaintext letter at the limit). He also invented what was probably the first automatic cipher device, a wheel which implemented a partial realization of his invention. In the Vigenère cipher, a polyalphabetic cipher, encryption uses a key word, which controls letter substitution depending on which letter of the key word is used. In the mid-19th century Charles Babbage showed that the Vigenère cipher was vulnerable to Kasiski examination, but this was first published about ten years later by Friedrich Kasiski.
Although frequency analysis can be a powerful and general technique against many ciphers, encryption has still often been effective in practice, as many a would-be cryptanalyst was unaware of the technique. Breaking a message without using frequency analysis essentially required knowledge of the cipher used and perhaps of the key involved, thus making espionage, bribery, burglary, defection, etc., more attractive approaches to the cryptanalytically uninformed. It was finally explicitly recognized in the 19th century that secrecy of a cipher's algorithm is not a sensible nor practical safeguard of message security; in fact, it was further realized that any adequate cryptographic scheme (including ciphers) should remain secure even if the adversary fully understands the cipher algorithm itself. Security of the key used should alone be sufficient for a good cipher to maintain confidentiality under an attack. This fundamental principle was first explicitly stated in 1883 by Auguste Kerckhoffs and is generally called Kerckhoffs's Principle; alternatively and more bluntly, it was restated by Claude Shannon, the inventor of information theory and the fundamentals of theoretical cryptography, as Shannon's Maxim—'the enemy knows the system'.
Different physical devices and aids have been used to assist with ciphers. One of the earliest may have been the scytale of ancient Greece, a rod supposedly used by the Spartans as an aid for a transposition cipher. In medieval times, other aids were invented such as the cipher grille, which was also used for a kind of steganography. With the invention of polyalphabetic ciphers came more sophisticated aids such as Alberti's own cipher disk, Johannes Trithemius' tabula recta scheme, and Thomas Jefferson's wheel cypher (not publicly known, and reinvented independently by Bazeries around 1900). Many mechanical encryption/decryption devices were invented early in the 20th century, and several patented, among them rotor machines—famously including the Enigma machine used by the German government and military from the late 1920s and during World War II. The ciphers implemented by better quality examples of these machine designs brought about a substantial increase in cryptanalytic difficulty after WWI.
Computer era
Prior to the early 20th century, cryptography was mainly concerned with linguistic and lexicographic patterns. Since then the emphasis has shifted, and cryptography now makes extensive use of mathematics, including aspects of information theory, computational complexity, statistics, combinatorics, abstract algebra, number theory, and finite mathematics generally. Cryptography is also a branch of engineering, but an unusual one since it deals with active, intelligent, and malevolent opposition; other kinds of engineering (e.g., civil or chemical engineering) need deal only with neutral natural forces. There is also active research examining the relationship between cryptographic problems and quantum physics.
Just as the development of digital computers and electronics helped in cryptanalysis, it made possible much more complex ciphers. Furthermore, computers allowed for the encryption of any kind of data representable in any binary format, unlike classical ciphers which only encrypted written language texts; this was new and significant. Computer use has thus supplanted linguistic cryptography, both for cipher design and cryptanalysis. Many computer ciphers can be characterized by their operation on binary bit sequences (sometimes in groups or blocks), unlike classical and mechanical schemes, which generally manipulate traditional characters (i.e., letters and digits) directly. However, computers have also assisted cryptanalysis, which has compensated to some extent for increased cipher complexity. Nonetheless, good modern ciphers have stayed ahead of cryptanalysis; it is typically the case that use of a quality cipher is very efficient (i.e., fast and requiring few resources, such as memory or CPU capability), while breaking it requires an effort many orders of magnitude larger, and vastly larger than that required for any classical cipher, making cryptanalysis so inefficient and impractical as to be effectively impossible.
Advent of modern cryptography
Cryptanalysis of the new mechanical devices proved to be both difficult and laborious. In the United Kingdom, cryptanalytic efforts at Bletchley Park during WWII spurred the development of more efficient means for carrying out repetitious tasks. This culminated in the development of the Colossus, the world's first fully electronic, digital, programmable computer, which assisted in the decryption of ciphers generated by the German Army's Lorenz SZ40/42 machine.
Extensive open academic research into cryptography is relatively recent; it began only in the mid-1970s. In recent times, IBM personnel designed the algorithm that became the Federal (i.e., US) Data Encryption Standard; Whitfield Diffie and Martin Hellman published their key agreement algorithm;[27] and the RSA algorithm was published in Martin Gardner's Scientific American column. Since then, cryptography has become a widely used tool in communications, computer networks, and computer security generally.
Some modern cryptographic techniques can only keep their keys secret if certain mathematical problems are intractable, such as the integer factorization or the discrete logarithm problems, so there are deep connections with abstract mathematics. There are very few cryptosystems that are proven to be unconditionally secure. The one-time pad is one, and was proven to be so by Claude Shannon. There are a few important algorithms that have been proven secure under certain assumptions. For example, the infeasibility of factoring extremely large integers is the basis for believing that RSA is secure, and some other systems, but even so, proof of unbreakability is unavailable since the underlying mathematical problem remains open. In practice, these are widely used, and are believed unbreakable in practice by most competent observers. There are systems similar to RSA, such as one by Michael O. Rabin that are provably secure provided factoring n = pq is impossible; it is quite unusable in practice. The discrete logarithm problem is the basis for believing some other cryptosystems are secure, and again, there are related, less practical systems that are provably secure relative to the solvability or insolvability discrete log problem.
As well as being aware of cryptographic history, cryptographic algorithm and system designers must also sensibly consider probable future developments while working on their designs. For instance, continuous improvements in computer processing power have increased the scope of brute-force attacks, so when specifying key lengths, the required key lengths are similarly advancing.[29] The potential effects of quantum computing are already being considered by some cryptographic system designers developing post-quantum cryptography; the announced imminence of small implementations of these machines may be making the need for preemptive caution rather more than merely speculative.
Modern cryptography
Symmetric-key cryptography
Symmetric-key cryptography refers to encryption methods in which both the sender and receiver share the same key (or, less commonly, in which their keys are different, but related in an easily computable way). This was the only kind of encryption publicly known until June 1976.
Symmetric key ciphers are implemented as either block ciphers or stream ciphers. A block cipher enciphers input in blocks of plaintext as opposed to individual characters, the input form used by a stream cipher.
The Data Encryption Standard (DES) and the Advanced Encryption Standard (AES) are block cipher designs that have been designated cryptography standards by the US government (though DES's designation was finally withdrawn after the AES was adopted).[30] Despite its deprecation as an official standard, DES (especially its still-approved and much more secure triple-DES variant) remains quite popular; it is used across a wide range of applications, from ATM encryption[31] to e-mail privacy[32] and secure remote access.[33] Many other block ciphers have been designed and released, with considerable variation in quality. Many, even some designed by capable practitioners, have been thoroughly broken, such as FEAL.
Stream ciphers, in contrast to the 'block' type, create an arbitrarily long stream of key material, which is combined with the plaintext bit-by-bit or character-by-character, somewhat like the one-time pad. In a stream cipher, the output stream is created based on a hidden internal state that changes as the cipher operates. That internal state is initially set up using the secret key material. RC4 is a widely used stream cipher.[4] Block ciphers can be used as stream ciphers by generating blocks of a keystream (in place of a Pseudorandom number generator) and applying an XOR operation to each bit of the plaintext with each bit of the keystream.
Message authentication codes (MACs) are much like cryptographic hash functions, except that a secret key can be used to authenticate the hash value upon receipt;[4] this additional complication blocks an attack scheme against bare digest algorithms, and so has been thought worth the effort. Cryptographic hash functions are a third type of cryptographic algorithm. They take a message of any length as input, and output a short, fixed-length hash, which can be used in (for example) a digital signature. For good hash functions, an attacker cannot find two messages that produce the same hash. MD4 is a long-used hash function that is now broken; MD5, a strengthened variant of MD4, is also widely used but broken in practice. The US National Security Agency developed the Secure Hash Algorithm series of MD5-like hash functions: SHA-0 was a flawed algorithm that the agency withdrew; SHA-1 is widely deployed and more secure than MD5, but cryptanalysts have identified attacks against it; the SHA-2 family improves on SHA-1, but is vulnerable to clashes as of 2011; and the US standards authority thought it "prudent" from a security perspective to develop a new standard to "significantly improve the robustness of NIST's overall hash algorithm toolkit."[36] Thus, a hash function design competition was meant to select a new U.S. national standard, to be called SHA-3, by 2012. The competition ended on October 2, 2012, when the NIST announced that Keccak would be the new SHA-3 hash algorithm.[37] Unlike block and stream ciphers that are invertible, cryptographic hash functions produce a hashed output that cannot be used to retrieve the original input data. Cryptographic hash functions are used to verify the authenticity of data retrieved from an untrusted source or to add a layer of security.
Public-key cryptography
Symmetric-key cryptosystems use the same key for encryption and decryption of a message, although a message or group of messages can have a different key than others. A significant disadvantage of symmetric ciphers is the key management necessary to use them securely. Each distinct pair of communicating parties must, ideally, share a different key, and perhaps for each ciphertext exchanged as well. The number of keys required increases as the square of the number of network members, which very quickly requires complex key management schemes to keep them all consistent and secret.
In a groundbreaking 1976 paper, Whitfield Diffie and Martin Hellman proposed the notion of public-key (also, more generally, called asymmetric key) cryptography in which two different but mathematically related keys are used—a public key and a private key.[38] A public key system is so constructed that calculation of one key (the 'private key') is computationally infeasible from the other (the 'public key'), even though they are necessarily related. Instead, both keys are generated secretly, as an interrelated pair.[39] The historian David Kahn described public-key cryptography as "the most revolutionary new concept in the field since polyalphabetic substitution emerged in the Renaissance".
In public-key cryptosystems, the public key may be freely distributed, while its paired private key must remain secret. In a public-key encryption system, the public key is used for encryption, while the private or secret key is used for decryption. While Diffie and Hellman could not find such a system, they showed that public-key cryptography was indeed possible by presenting the Diffie–Hellman key exchange protocol, a solution that is now widely used in secure communications to allow two parties to secretly agree on a shared encryption key.[27] The X.509 standard defines the most commonly used format for public key certificates.
Diffie and Hellman's publication sparked widespread academic efforts in finding a practical public-key encryption system. This race was finally won in 1978 by Ronald Rivest, Adi Shamir, and Len Adleman, whose solution has since become known as the RSA algorithm.
The Diffie–Hellman and RSA algorithms, in addition to being the first publicly known examples of high-quality public-key algorithms, have been among the most widely used. Other asymmetric-key algorithms include the Cramer–Shoup cryptosystem, ElGamal encryption, and various elliptic curve techniques.
A document published in 1997 by the Government Communications Headquarters (GCHQ), a British intelligence organization, revealed that cryptographers at GCHQ had anticipated several academic developments.[43] Reportedly, around 1970, James H. Ellis had conceived the principles of asymmetric key cryptography. In 1973, Clifford Cocks invented a solution that was very similar in design rationale to RSA.[43][44] In 1974, Malcolm J. Williamson is claimed to have developed the Diffie–Hellman key exchange.
ublic-key cryptography is also used for implementing digital signature schemes. A digital signature is reminiscent of an ordinary signature; they both have the characteristic of being easy for a user to produce, but difficult for anyone else to forge. Digital signatures can also be permanently tied to the content of the message being signed; they cannot then be 'moved' from one document to another, for any attempt will be detectable. In digital signature schemes, there are two algorithms: one for signing, in which a secret key is used to process the message (or a hash of the message, or both), and one for verification, in which the matching public key is used with the message to check the validity of the signature. RSA and DSA are two of the most popular digital signature schemes. Digital signatures are central to the operation of public key infrastructures and many network security schemes (e.g., SSL/TLS, many VPNs, etc.).[34]
Public-key algorithms are most often based on the computational complexity of "hard" problems, often from number theory. For example, the hardness of RSA is related to the integer factorization problem, while Diffie–Hellman and DSA are related to the discrete logarithm problem. The security of elliptic curve cryptography is based on number theoretic problems involving elliptic curves. Because of the difficulty of the underlying problems, most public-key algorithms involve operations such as modular multiplication and exponentiation, which are much more computationally expensive than the techniques used in most block ciphers, especially with typical key sizes. As a result, public-key cryptosystems are commonly hybrid cryptosystems, in which a fast high-quality symmetric-key encryption algorithm is used for the message itself, while the relevant symmetric key is sent with the message, but encrypted using a public-key algorithm. Similarly, hybrid signature schemes are often used, in which a cryptographic hash function is computed, and only the resulting hash is digitally signed.[4]
Cryptographic Hash Functions
Cryptographic Hash Functions are cryptographic algorithms that are ways to generate and utilize specific keys to encrypt data for either symmetric or asymmetric encryption, and such functions may be viewed as keys themselves. They take a message of any length as input, and output a short, fixed-length hash, which can be used in (for example) a digital signature. For good hash functions, an attacker cannot find two messages that produce the same hash. MD4 is a long-used hash function that is now broken; MD5, a strengthened variant of MD4, is also widely used but broken in practice. The US National Security Agency developed the Secure Hash Algorithm series of MD5-like hash functions: SHA-0 was a flawed algorithm that the agency withdrew; SHA-1 is widely deployed and more secure than MD5, but cryptanalysts have identified attacks against it; the SHA-2 family improves on SHA-1, but is vulnerable to clashes as of 2011; and the US standards authority thought it "prudent" from a security perspective to develop a new standard to "significantly improve the robustness of NIST's overall hash algorithm toolkit."[36] Thus, a hash function design competition was meant to select a new U.S. national standard, to be called SHA-3, by 2012. The competition ended on October 2, 2012, when the NIST announced that Keccak would be the new SHA-3 hash algorithm.[37] Unlike block and stream ciphers that are invertible, cryptographic hash functions produce a hashed output that cannot be used to retrieve the original input data. Cryptographic hash functions are used to verify the authenticity of data retrieved from an untrusted source or to add a layer of security.
Cryptanalysis
The goal of cryptanalysis is to find some weakness or insecurity in a cryptographic scheme, thus permitting its subversion or evasion.
It is a common misconception that every encryption method can be broken. In connection with his WWII work at Bell Labs, Claude Shannon proved that the one-time pad cipher is unbreakable, provided the key material is truly random, never reused, kept secret from all possible attackers, and of equal or greater length than the message.[46] Most ciphers, apart from the one-time pad, can be broken with enough computational effort by brute force attack, but the amount of effort needed may be exponentially dependent on the key size, as compared to the effort needed to make use of the cipher. In such cases, effective security could be achieved if it is proven that the effort required (i.e., "work factor", in Shannon's terms) is beyond the ability of any adversary. This means it must be shown that no efficient method (as opposed to the time-consuming brute force method) can be found to break the cipher. Since no such proof has been found to date, the one-time-pad remains the only theoretically unbreakable cipher. Although well-implemented one-time-pad encryption cannot be broken, traffic analysis is still possible.
There are a wide variety of cryptanalytic attacks, and they can be classified in any of several ways. A common distinction turns on what Eve (an attacker) knows and what capabilities are available. In a ciphertext-only attack, Eve has access only to the ciphertext (good modern cryptosystems are usually effectively immune to ciphertext-only attacks). In a known-plaintext attack, Eve has access to a ciphertext and its corresponding plaintext (or to many such pairs). In a chosen-plaintext attack, Eve may choose a plaintext and learn its corresponding ciphertext (perhaps many times); an example is gardening, used by the British during WWII. In a chosen-ciphertext attack, Eve may be able to choose ciphertexts and learn their corresponding plaintexts.[4] Finally in a man-in-the-middle attack Eve gets in between Alice (the sender) and Bob (the recipient), accesses and modifies the traffic and then forwards it to the recipient.[47] Also important, often overwhelmingly so, are mistakes (generally in the design or use of one of the protocols involved).
Cryptanalysis of symmetric-key ciphers typically involves looking for attacks against the block ciphers or stream ciphers that are more efficient than any attack that could be against a perfect cipher. For example, a simple brute force attack against DES requires one known plaintext and 255 decryptions, trying approximately half of the possible keys, to reach a point at which chances are better than even that the key sought will have been found. But this may not be enough assurance; a linear cryptanalysis attack against DES requires 243 known plaintexts (with their corresponding ciphertexts) and approximately 243 DES operations.[48] This is a considerable improvement over brute force attacks.
Public-key algorithms are based on the computational difficulty of various problems. The most famous of these are the difficulty of integer factorization of semiprimes and the difficulty of calculating discrete logarithms, both of which are not yet proven to be solvable in polynomial time (P) using only a classical Turing-complete computer. Much public-key cryptanalysis concerns designing algorithms in P that can solve these problems, or using other technologies, such as quantum computers. For instance, the best-known algorithms for solving the elliptic curve-based version of discrete logarithm are much more time-consuming than the best-known algorithms for factoring, at least for problems of more or less equivalent size. Thus, to achieve an equivalent strength of encryption, techniques that depend upon the difficulty of factoring large composite numbers, such as the RSA cryptosystem, require larger keys than elliptic curve techniques. For this reason, public-key cryptosystems based on elliptic curves have become popular since their invention in the mid-1990s.
While pure cryptanalysis uses weaknesses in the algorithms themselves, other attacks on cryptosystems are based on actual use of the algorithms in real devices, and are called side-channel attacks. If a cryptanalyst has access to, for example, the amount of time the device took to encrypt a number of plaintexts or report an error in a password or PIN character, he may be able to use a timing attack to break a cipher that is otherwise resistant to analysis. An attacker might also study the pattern and length of messages to derive valuable information; this is known as traffic analysis[49] and can be quite useful to an alert adversary. Poor administration of a cryptosystem, such as permitting too short keys, will make any system vulnerable, regardless of other virtues. Social engineering and other attacks against humans (e.g., bribery, extortion, blackmail, espionage, torture, ...) are usually employed due to being more cost-effective and feasible to perform in a reasonable amount of time compared to pure cryptanalysis by a high margin.
Cryptographic primitives
Much of the theoretical work in cryptography concerns cryptographic primitives—algorithms with basic cryptographic properties—and their relationship to other cryptographic problems. More complicated cryptographic tools are then built from these basic primitives. These primitives provide fundamental properties, which are used to develop more complex tools called cryptosystems or cryptographic protocols, which guarantee one or more high-level security properties. Note, however, that the distinction between cryptographic primitives and cryptosystems, is quite arbitrary; for example, the RSA algorithm is sometimes considered a cryptosystem, and sometimes a primitive. Typical examples of cryptographic primitives include pseudorandom functions, one-way functions, etc.
Cryptosystems
One or more cryptographic primitives are often used to develop a more complex algorithm, called a cryptographic system, or cryptosystem. Cryptosystems (e.g., El-Gamal encryption) are designed to provide particular functionality (e.g., public key encryption) while guaranteeing certain security properties (e.g., chosen-plaintext attack (CPA) security in the random oracle model). Cryptosystems use the properties of the underlying cryptographic primitives to support the system's security properties. As the distinction between primitives and cryptosystems is somewhat arbitrary, a sophisticated cryptosystem can be derived from a combination of several more primitive cryptosystems. In many cases, the cryptosystem's structure involves back and forth communication among two or more parties in space (e.g., between the sender of a secure message and its receiver) or across time (e.g., cryptographically protected backup data). Such cryptosystems are sometimes called cryptographic protocols.
Some widely known cryptosystems include RSA, Schnorr signature, ElGamal encryption, and Pretty Good Privacy (PGP). More complex cryptosystems include electronic cash[50] systems, signcryption systems, etc. Some more 'theoretical'[clarification needed] cryptosystems include interactive proof systems,[51] (like zero-knowledge proofs),[52] systems for secret sharing,[53][54] etc.
Lightweight cryptography
Lightweight cryptography (LWC) concerns cryptographic algorithms developed for a strictly constrained environment. The growth of Internet of Things (IoT) has spiked research into the development of lightweight algorithms that are better suited for the environment. An IoT environment requires strict constraints on power consumption, processing power, and security.[55] Algorithms such as PRESENT, AES, and SPECK are examples of the many LWC algorithms that have been developed to achieve the standard set by the National Institute of Standards and Technology.[56]
Applications
In general
To ensure secrecy during transmission, many systems use private key cryptography to protect transmitted information. With public-key systems, one can maintain secrecy without a master key or a large number of keys
In cybersecurity
Cryptography can be used to secure communications by encrypting them. Websites use encryption via HTTPS.[58] "End-to-end" encryption, where only sender and receiver can read messages, is implemented for email in Pretty Good Privacy and for secure messaging in general in Signal and WhatsApp.[58]
Operating systems use encryption to keep passwords secret, conceal parts of the system, and ensure that software updates are truly from the system maker.[58] Instead of storing plaintext passwords, computer systems store hashes thereof; then, when a user logs in, the system passes the given password through a cryptographic hash function and compares it to the hashed value on file. In this manner, neither the system nor an attacker has at any point access to the password in plaintext.[58]
Encryption is sometimes used to encrypt one's entire drive. For example, University College London has implemented BitLocker (a program by Microsoft) to render drive data opaque without users logging in.[58]
Legal issues
Prohibitions
Cryptography has long been of interest to intelligence gathering and law enforcement agencies.[8] Secret communications may be criminal or even treasonous[citation needed]. Because of its facilitation of privacy, and the diminution of privacy attendant on its prohibition, cryptography is also of considerable interest to civil rights supporters. Accordingly, there has been a history of controversial legal issues surrounding cryptography, especially since the advent of inexpensive computers has made widespread access to high-quality cryptography possible.
In some countries, even the domestic use of cryptography is, or has been, restricted. Until 1999, France significantly restricted the use of cryptography domestically, though it has since relaxed many of these rules. In China and Iran, a license is still required to use cryptography.[6] Many countries have tight restrictions on the use of cryptography. Among the more restrictive are laws in Belarus, Kazakhstan, Mongolia, Pakistan, Singapore, Tunisia, and Vietnam.[59]
In the United States, cryptography is legal for domestic use, but there has been much conflict over legal issues related to cryptography.[8] One particularly important issue has been the export of cryptography and cryptographic software and hardware. Probably because of the importance of cryptanalysis in World War II and an expectation that cryptography would continue to be important for national security, many Western governments have, at some point, strictly regulated export of cryptography. After World War II, it was illegal in the US to sell or distribute encryption technology overseas; in fact, encryption was designated as auxiliary military equipment and put on the United States Munitions List.[60] Until the development of the personal computer, asymmetric key algorithms (i.e., public key techniques), and the Internet, this was not especially problematic. However, as the Internet grew and computers became more widely available, high-quality encryption techniques became well known around the globe.
Export controls
In the 1990s, there were several challenges to US export regulation of cryptography. After the source code for Philip Zimmermann's Pretty Good Privacy (PGP) encryption program found its way onto the Internet in June 1991, a complaint by RSA Security (then called RSA Data Security, Inc.) resulted in a lengthy criminal investigation of Zimmermann by the US Customs Service and the FBI, though no charges were ever filed.[61][62] Daniel J. Bernstein, then a graduate student at UC Berkeley, brought a lawsuit against the US government challenging some aspects of the restrictions based on free speech grounds. The 1995 case Bernstein v. United States ultimately resulted in a 1999 decision that printed source code for cryptographic algorithms and systems was protected as free speech by the United States Constitution.[63]
In 1996, thirty-nine countries signed the Wassenaar Arrangement, an arms control treaty that deals with the export of arms and "dual-use" technologies such as cryptography. The treaty stipulated that the use of cryptography with short key-lengths (56-bit for symmetric encryption, 512-bit for RSA) would no longer be export-controlled.[64] Cryptography exports from the US became less strictly regulated as a consequence of a major relaxation in 2000;[65] there are no longer very many restrictions on key sizes in US-exported mass-market software. Since this relaxation in US export restrictions, and because most personal computers connected to the Internet include US-sourced web browsers such as Firefox or Internet Explorer, almost every Internet user worldwide has potential access to quality cryptography via their browsers (e.g., via Transport Layer Security). The Mozilla Thunderbird and Microsoft Outlook E-mail client programs similarly can transmit and receive emails via TLS, and can send and receive email encrypted with S/MIME. Many Internet users don't realize that their basic application software contains such extensive cryptosystems. These browsers and email programs are so ubiquitous that even governments whose intent is to regulate civilian use of cryptography generally don't find it practical to do much to control distribution or use of cryptography of this quality, so even when such laws are in force, actual enforcement is often effectively impossible.[citation needed]
NSA involvement
Another contentious issue connected to cryptography in the United States is the influence of the National Security Agency on cipher development and policy.[8] The NSA was involved with the design of DES during its development at IBM and its consideration by the National Bureau of Standards as a possible Federal Standard for cryptography.[66] DES was designed to be resistant to differential cryptanalysis,[67] a powerful and general cryptanalytic technique known to the NSA and IBM, that became publicly known only when it was rediscovered in the late 1980s.[68] According to Steven Levy, IBM discovered differential cryptanalysis,[62] but kept the technique secret at the NSA's request. The technique became publicly known only when Biham and Shamir re-discovered and announced it some years later. The entire affair illustrates the difficulty of determining what resources and knowledge an attacker might actually have.
Another instance of the NSA's involvement was the 1993 Clipper chip affair, an encryption microchip intended to be part of the Capstone cryptography-control initiative. Clipper was widely criticized by cryptographers for two reasons. The cipher algorithm (called Skipjack) was then classified (declassified in 1998, long after the Clipper initiative lapsed). The classified cipher caused concerns that the NSA had deliberately made the cipher weak in order to assist its intelligence efforts. The whole initiative was also criticized based on its violation of Kerckhoffs's Principle, as the scheme included a special escrow key held by the government for use by law enforcement (i.e. wiretapping).
Digital rights management
Cryptography is central to digital rights management (DRM), a group of techniques for technologically controlling use of copyrighted material, being widely implemented and deployed at the behest of some copyright holders. In 1998, U.S. President Bill Clinton signed the Digital Millennium Copyright Act (DMCA), which criminalized all production, dissemination, and use of certain cryptanalytic techniques and technology (now known or later discovered); specifically, those that could be used to circumvent DRM technological schemes.[69] This had a noticeable impact on the cryptography research community since an argument can be made that any cryptanalytic research violated the DMCA. Similar statutes have since been enacted in several countries and regions, including the implementation in the EU Copyright Directive. Similar restrictions are called for by treaties signed by World Intellectual Property Organization member-states.
The United States Department of Justice and FBI have not enforced the DMCA as rigorously as had been feared by some, but the law, nonetheless, remains a controversial one. Niels Ferguson, a well-respected cryptography researcher, has publicly stated that he will not release some of his research into an Intel security design for fear of prosecution under the DMCA.[70] Cryptologist Bruce Schneier has argued that the DMCA encourages vendor lock-in, while inhibiting actual measures toward cyber-security.[71] Both Alan Cox (longtime Linux kernel developer) and Edward Felten (and some of his students at Princeton) have encountered problems related to the Act. Dmitry Sklyarov was arrested during a visit to the US from Russia, and jailed for five months pending trial for alleged violations of the DMCA arising from work he had done in Russia, where the work was legal. In 2007, the cryptographic keys responsible for Blu-ray and HD DVD content scrambling were discovered and released onto the Internet. In both cases, the Motion Picture Association of America sent out numerous DMCA takedown notices, and there was a massive Internet backlash[9] triggered by the perceived impact of such notices on fair use and free speech.
Forced disclosure of encryption keys
In the United Kingdom, the Regulation of Investigatory Powers Act gives UK police the powers to force suspects to decrypt files or hand over passwords that protect encryption keys. Failure to comply is an offense in its own right, punishable on conviction by a two-year jail sentence or up to five years in cases involving national security.[7] Successful prosecutions have occurred under the Act; the first, in 2009,[72] resulted in a term of 13 months' imprisonment.[73] Similar forced disclosure laws in Australia, Finland, France, and India compel individual suspects under investigation to hand over encryption keys or passwords during a criminal investigation.
In the United States, the federal criminal case of United States v. Fricosu addressed whether a search warrant can compel a person to reveal an encryption passphrase or password.[74] The Electronic Frontier Foundation (EFF) argued that this is a violation of the protection from self-incrimination given by the Fifth Amendment.[75] In 2012, the court ruled that under the All Writs Act, the defendant was required to produce an unencrypted hard drive for the court.[76]
In many jurisdictions, the legal status of forced disclosure remains unclear.
The 2016 FBI–Apple encryption dispute concerns the ability of courts in the United States to compel manufacturers' assistance in unlocking cell phones whose contents are cryptographically protected.
As a potential counter-measure to forced disclosure some cryptographic software supports plausible deniability, where the encrypted data is indistinguishable from unused random data (for example such as that of a drive which has been securely wiped).
Smart contract
A smart contract is a computer program or a transaction protocol which is intended to automatically execute, control or document legally relevant events and actions according to the terms of a contract or an agreement. The objectives of smart contracts are the reduction of need in trusted intermediators, arbitrations and enforcement costs, fraud losses, as well as the reduction of malicious and accidental exceptions.
Vending machines are mentioned as the oldest piece of technology equivalent to smart contract implementation.2014's white paper about the cryptocurrency Ethereum describes the Bitcoin protocol as a weak version of the smart contract concept as defined by computer scientist, lawyer and cryptographer Nick Szabo. Since Bitcoin, various cryptocurrencies support scripting languages which allow for more advanced smart contracts between untrusted parties. Smart contracts should be distinguished from smart legal contracts. The latter refers to a traditional natural language legally-binding agreement which has certain terms expressed and implemented in machine-readable code.
Etymology
Smart contracts were first proposed in the early 1990s by Nick Szabo, who coined the term, using it to refer to "a set of promises, specified in digital form, including protocols within which the parties perform on these promises".[11][12] In 1998, the term was used to describe objects in rights management service layer of the system The Stanford Infobus, which was a part of Stanford Digital Library Project.
Legal status of smart contracts
A smart contract does not necessarily constitute a valid binding agreement at law.[13] Some legal academics claim that smart contracts are not legal agreements, but rather means of performing obligations deriving from other agreements[14] such as technological means for the automation of payment obligations[15] or obligations consisting in the transfer of tokens or cryptocurrencies. Additionally, other scholars have argued that the imperative or declarative nature of programming languages can impact the legal validity of smart contracts.
Since the 2015 launch of the Ethereum blockchain,[17] the term "smart contract" has been more specifically applied toward the notion of general purpose computation that takes place on a blockchain or distributed ledger. The US National Institute of Standards and Technology describes a "smart contract" as a "collection of code and data (sometimes referred to as functions and state) that is deployed using cryptographically signed transactions on the blockchain network".[18] In this interpretation, used for example by the Ethereum Foundation[6] or IBM,[19] a smart contract is not necessarily related to the classical concept of a contract, but can be any kind of computer program. A smart contract also can be regarded as a secured stored procedure as its execution and codified effects like the transfer of some value between parties are strictly enforced and can not be manipulated, after a transaction with specific contract details is stored into a blockchain or distributed ledger. That's because the actual execution of contracts is controlled and audited by the platform, not by any arbitrary server-side programs connecting to the platform.
In 2017, by implementing the Decree on Development of Digital Economy, Belarus has become the first-ever country to legalize smart contracts. Belarusian lawyer Denis Aleinikov is considered to be the author of a smart contract legal concept introduced by the decree.
In 2018, a US Senate report said: "While smart contracts might sound new, the concept is rooted in basic contract law. Usually, the judicial system adjudicates contractual disputes and enforces terms, but it is also common to have another arbitration method, especially for international transactions. With smart contracts, a program enforces the contract built into the code."[23] A number of states in the US have passed legislation on the use of smart contracts, such as Arizona,[24] Nevada,[25] Tennessee,[26] and Wyoming.[citation needed][27] And in April 2020, Iowa's House of Representatives passed a bill legally recognizing smart contacts in the state.
In April 2021, the UK Jurisdiction Taskforce (UKJT) published the Digital Dispute Resolution Rules (the Digital DR Rules) to help enable the rapid resolution of blockchain and crypto legal disputes in Britain.
Workings
Similar to a transfer of value on a blockchain, deployment of a smart contract on a blockchain occurs by sending a transaction from a wallet for the blockchain.[30] The transaction includes the compiled code for the smart contract as well as a special receiver address.[30] That transaction must then be included in a block that is added to the blockchain, at which point the smart contract's code will execute to establish the initial state of the smart contract.[30] Byzantine fault-tolerant algorithms secure the smart contract in a decentralized way from attempts to tamper with it. Once a smart contract is deployed, it cannot be updated.[31] Smart contracts on a blockchain can store arbitrary state and execute arbitrary computations. End clients interact with a smart contract through transactions. Such transactions with a smart contract can invoke other smart contracts. These transactions might result in changing the state and sending coins from one smart contract to another or from one account to another.[31]
The most popular blockchain for running smart contracts is Ethereum.[32] On Ethereum, smart contracts are typically written in a Turing-complete programming language called Solidity,[33] and compiled into low-level bytecode to be executed by the Ethereum Virtual Machine.[34] Due to the halting problem and other security problems, Turing-completeness is considered to be a risk and is deliberately avoided by languages like Vyper.[35][36] Some of the other smart contract programming languages missing Turing-completeness are Simplicity, Scilla, Ivy and Bitcoin Script.[36] However, measurements using regular expressions showed that only 35.3% of 53,757 Ethereum smart contracts included recursions and loops — constructs connected to the halting problem.[37]
Several languages are designed to enable formal verification: Bamboo, IELE, Simplicity, Michelson (can be verified with Coq),[36] Liquidity (compiles to Michelson), Scilla, DAML and Pact.[35]
Processes on a blockchain are generally deterministic in order to ensure Byzantine fault-tolerance.[40] Nevertheless, real world application of smart contracts, such as lotteries and casinos, require secure randomness.[41] In fact, blockchain technology reduces the costs for conducting of a lottery and is therefore beneficial for the participants. Randomness on blockchain can be implemented by using block hashes or timestamps, oracles, commitment schemes, special smart contracts like RANDAO[42][43] and Quanta as well as sequences from mixed strategy Nash equilibria.[40]
Applications
In 1998, Szabo proposed that smart contract infrastructure can be implemented by replicated asset registries and contract execution using cryptographic hash chains and Byzantine fault-tolerant replication.[44] Askemos implemented this approach in 2002[45][46] using Scheme (later adding SQLite[47][48]) as contract script language.
One proposal for using bitcoin for replicated asset registration and contract execution is called "colored coins".[50] Replicated titles for potentially arbitrary forms of property, along with replicated contract execution, are implemented in different projects.
As of 2015, UBS was experimenting with "smart bonds" that use the bitcoin blockchain[51] in which payment streams could hypothetically be fully automated, creating a self-paying instrument.
Inheritance wishes could hypothetically be implemented automatically upon registration of a death certificate by means of smart contracts.[53][54] Birth certificates can also work together with smart contracts.
Smart contracts can also be used to handle real estate transactions [57] (i.e. via Propy, ...)[58] [59] and blockchain solutions are also proliferating on the field of title records and in the public register.
Smart contracts can also be used in employment contracts, especially temporary employment contracts, offering benefits for both employer and employee.
Security issues
A blockchain-based smart contract is visible to all users of said blockchain. However, this leads to a situation where bugs, including security holes, are visible to all yet may not be quickly fixed.[67] Such an attack, difficult to fix quickly, was successfully executed on The DAO in June 2016, draining approximately US$50 million worth of Ether at the time, while developers attempted to come to a solution that would gain consensus.[68] The DAO program had a time delay in place before the hacker could remove the funds; a hard fork of the Ethereum software was done to claw back the funds from the attacker before the time limit expired.[69] Other high-profile attacks include the Parity multisignature wallet attacks, and an integer underflow/overflow attack (2018), totaling over US$184 million.
Issues in Ethereum smart contracts, in particular, include ambiguities and easy-but-insecure constructs in its contract language Solidity, compiler bugs, Ethereum Virtual Machine bugs, attacks on the blockchain network, the immutability of bugs and that there is no central source documenting known vulnerabilities, attacks and problematic constructs.[39]
Difference from smart legal contracts
Smart legal contracts are distinct from smart contracts. As mentioned above, a smart contract is not necessarily legally enforceable as a contract. On the other hand, a smart legal contract has all the elements of a legally enforceable contract in the jurisdiction in which it can be enforced and it can be enforced by a court or tribunal. Therefore, while every smart legal contract will contain some elements of a smart contract, not every smart contract will be a smart legal contract.
There is no formal definition of a smart legal contract in the legal industry.
A Ricardian contract is a type of smart legal contract.
Blockchain Interoperability : Why Is Cross Chain Technology Important?
Blockchain and distributed ledger networks are exploding by the day. Interconnecting these new chains is becoming a necessity as more people continue to take note of the emerging technology and its capabilities. Let’s dive in deeper to see what is blockchain interoperability and why does it matter so much.
The number of blockchain projects is on the rise in part because developers are thinking outside the box as they try to leverage the technology’s capabilities. The increase also comes on acknowledgment that no perfect solution will be able to address all blockchain needs at once.
A perfect example is the IOTA blockchain that seeks to enhance payments on the Internet of Things. VeChain, on the other hand, shares similar capabilities but with the aim of strengthening supply chain management on the blockchain. Stellar blockchain, on the other hand, seeks to make it easy for people to come up with a global payment network for solving low latency issues in remote areas.
Amidst the proliferation of blockchain projects, one thing stands out. All blockchains as well as ledgers and DAGs perform a different set of transactions and handle different amounts of data processing. It is also becoming increasingly clear that there are different networks and blockchains designed for specific labor unions, religions, community organizations as well as government departments.
The rapid development of blockchain is set to give rise to many different kinds of chains. One such technology that is becoming increasingly evident is Cross Chain Technology.
Blockchain Interoperability: What is Cross Chain Technology?
Cross Chain, technology is increasingly becoming a hot topic of discussion seen as the ultimate solution for enhancing interoperability between blockchains. In Layman terms, a Cross-chain Technology is an emerging technology that seeks to allow transmission of value and information between different blockchain networks.
Increased usage of established networks like Ripple, Bitcoin, and Ethereum while a good thing has given rise to many issues key among them being economical and technical scaling limitations. As discussed above most blockchain networks operate on isolated ecosystems as they address they try to resolve a unique set of needs.
The fact that the chains operate in isolation has mostly made it impossible for people to enjoy the full benefits the ledger technology. The inability of different blockchains to communicate with one another has made it impossible for people to enjoy the full benefits of blockchain technology. Cross chain, technology seeks to solve all these issues, by enabling interoperability between blockchains thus making it easy for them to communicate with one another and share information.
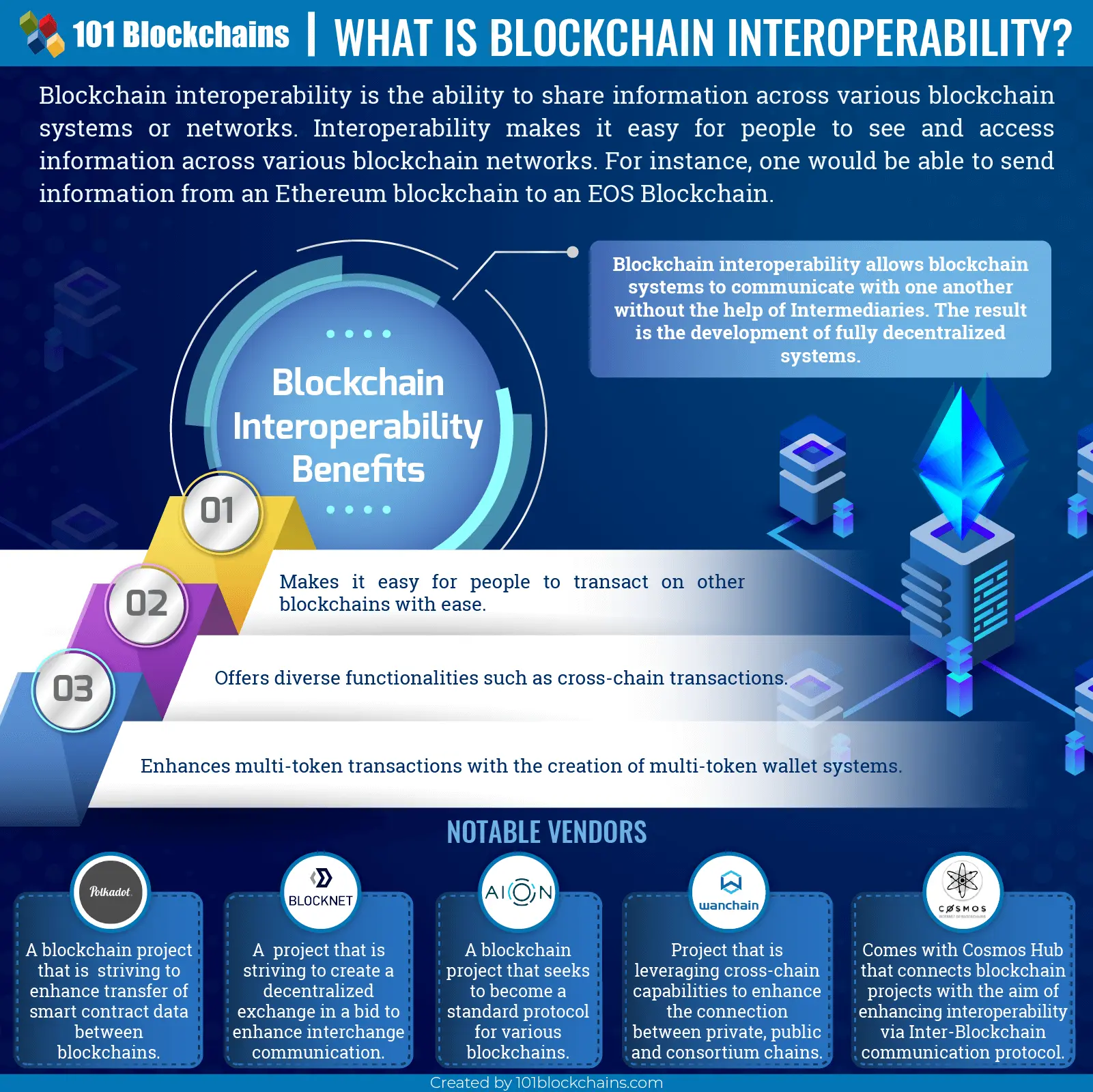
Cross Blockchain Compatibility
Cross-chain, protocol ensures interoperability between blockchains, thus enabling the exchange of value as well as information between various networks. Complimented with the benefits of public decentralized chains, such protocols should lay the foundation for blockchain mass adoption and use
Cross blockchain compatibility, allows different blockchains to communicate with one another without the help of intermediaries. What this means is that blockchains sharing similar networks will be able to transfer value between each other.
While in use in a business ecosystem, businesses will no longer have to contend only with clients on a network the business as built on. Instead, companies will be able to transact with clients from other compatible blockchains. The entire process will take place without any downtime or expensive transaction fees. Just as is the case with the Internet of value, cross blockchain compatibility will accord blockchain networks an effective means of value transmission.
Who Is Leveraging Cross-Chain Technology?
Ripple is an excellent example of a blockchain project trying to explore cross chain transactions. While it is still in the early days of development, Ripple is trying to make it possible for people and entities to exchange various digital assets across different blockchains.
For starters, Ripple has already started helping banks, around the world, settle cross-border payments with one another across different currencies and cryptocurrencies. However, the blockchain project faces an uphill task to polish its cross-chain technology.
Importance of Blockchain Interoperability
The success of blockchain technology will come down to how different blockchain networks can interact and integrate. For that reason, interoperability between blockchains is the concept by which different blockchains communicate with one another all in the effort of enabling smooth sharing of information.
Interoperability is essentially the ability to see and access information across various blockchain systems. For example, should a person send data to another blockchain, the recipient should be able to read it, comprehend and react with little effort? However, that is not possible, at the moment, as it is impossible to share information between says Bitcoin and Ethereum blockchains.
Cross Chain, technology seeks to solve all this by enhancing interoperability between blockchains. Emerging projects are slowly buying the idea as they attempt to come up with platforms that can communicate with one another without the need of a third party.
Blockchain interoperability should go a long way in getting rid of intermediaries or third parties, synonymous with centralized systems. The ability of different decentralized networks to communicate with one another without any intermediaries should thus go a long way in giving rise to fully decentralized systems.
Why Though?
Interoperability of blockchains is of great importance, as it will go a long way in making it easy for people to transact on other blockchains seamless. Currently one can only transact on one blockchain at a go i.e. Bitcoin or Ethereum. However, transferring information between two different chains is not possible.
Diverse Functionalities should come into being because of interoperability of blockchains. For starters, people will be able to make payments across multiple blockchains. A fully perfect blockchain interoperability project should thus be the core of the digital economy in future.
Blockchain Interoperability should also lead to multi-token transactions thanks to the development of multi-token wallet systems. Such a development will allow users to rely on a single wallet system to for storage and transfer of tokens with ease across various blockchains.
Blockchain Interoperability Projects
Given the ever-growing need to enhance the connection between various blockchain networks, many developers are already working on optimal solutions. The number of blockchain interoperability projects is on the rise as a result as developers look to accelerate blockchain mass adoption. Below are some of the top projects, looking to enhance blockchain interoperability.
Polkadot blockchain
Polkadot blockchain is a high-profile multi-chain technology taking blockchain interoperability to another level. A brainchild of Gavid Wood, one of the founders of Ethereum, Polkadot seeks to enhance the transfer of smart contract data through various blockchains.
Polkadot consists of multiple parachains that differ in characteristics. In Polkadot blockchain, transactions can be spread over a wide area given the number of chains in the network. All this is done while ensuring high levels of security on dealings.
Polkadot Blockchain interoperability project seeks to ensure a seamless connection between private chains, public networks, oracles as well as permission less interface. The developers behind the blockchain interoperability solutions want to enable an internet where independent blockchain solutions will be able to exchange information via a Polkadot relay chain.
The fundamental tenets of the blockchain interoperability solutions are scalability as well as governance.
Blocknet
Developers behind Blocknet are currently working on creating a decentralized exchange all in the effort of enhancing interchange communication.
Blockchain is also implementing blockchain interoperability strategies that can change the way we see blockchain at the moment.
What Blocknet intends to do is decentralize all the four components all in the effort of creating the first Decentralized exchange. The project backers are also working on optimizing the cross-chain platform to serve as infrastructure.
Aion Online
Aion online is another high profile Blockchain interoperability project that seeks to address unresolved questions around scalability and interoperability in blockchain networks. Developers are planning to position Aion as the standard protocol used by various blockchains. The end game is to enhance the creation of efficient and decentralized systems.
The developers have already come up with a federated blockchain network that makes it possible to integrate disparate blockchain systems in multi-tier hub.
Wanchain
Wanchain casts itself as the world’s first online blockchain interoperable blockchain solution, with secure multi-party computing. More so, the blockchain interoperability solution seeks to rebuild finance by housing all digital assets on one blockchain.
They are introducing one of the unique blockchain interoperability strategies at the moment.
The blockchain interoperability project ensures cross-chain capabilities by leveraging the latest research in cryptographic theories. It also relies on a proprietary protocol that allows interconnection of private, public and consortium chains. The interconnection makes it easy to transfer digital assets between two different blockchains.
Based on Ethereum, Wanchain blockchain also enables the deployment of smart contracts. All these aspects make it a compelling blockchain solution for delivering distributed applications that require easy access to different blockchains. Privacy on the blockchain is enhanced by the use of Ring signatures as well as one-time stealth addresses.
Cosmos Blockchain
Cosmos blockchain is the most underrated blockchain interoperability project. The blockchain project is in the race to become the hub of many projects. The developers have since released a software development kit that they say will address scalability and interoperability issues in blockchain projects.
Cosmos blockchain architecture consists of several independent blockchains called Zones, attached to a central blockchain dubbed as the Hub. Tendermint Core that enables high-performance as well as consistent and secure PBFT-like consensus engine, powers each Zone in this case.
The cosmos Hub connects blockchain projects to enhance interoperability via the Inter-Blockchain communication protocol.
Because of the interconnection, people can send tokens from one zone to another in real time and securely, without engaging the services of a third party. Cosmos blockchain can connect different zones from public to private project thanks to the IBC connection.
Blockchain Interoperability Challenges and Probable Solutions
The biggest challenges to blockchain interoperability are the fact that there are many blockchain systems, which do not speak the same language. For starters, many complex platforms in use come with varying levels of smart contract use. Transaction scheme, as well as consensus models in these projects, also differ a great deal, for any form of interconnection to happen.
To overcome some of the underlying issues crippling blockchain interoperability, then there is a need to turn to a technology that enables universal communication between various blockchains. More so, the use of open protocols, as well as Multi Chain Frameworks, are touted as possible solutions to blockchain interoperability issues.
Open Protocols to Enhance Blockchain Interoperability
We think this is one of the best solutions for the interoperability issues. The use of open Protocols should go a long way in enabling standardized pathways through which various blockchains can communicate with one another with ease. Such protocols provide the universal language for blockchains that enhance communication.
A perfect example of an Open Protocol for blockchain interoperability is the Atomic Swap. Acting as decentralized escrow cross chain, Atomic Swap makes it possible to exchange value between two varying blockchains such as 1BTC for 1ETH. The whole transaction takes place without the use of an exchange or an intermediary. Interledger is another example of cross chain blockchain that utilizes atomic swap protocol.
Use of Multi-Chain Frameworks
Multi-Chain frameworks on the other hand act as open environments through which blockchains plug into. Unlike Open Protocols, they are more complicated. However, they help facilitate open communication and transfer of both value and data between different blockchains.
With Multi Chain Frameworks, blockchains can plug and become part of a standardized ecosystem to be able to share information. It is for this reason that most of the time they are called the Internet of blockchains as they offer unique and promising capabilities when it comes to blockchain interoperability.
Bottom Line
Cross chain technology and blockchain interoperability are essential aspects of blockchain technology as discussed above. The two concepts are poised to not only widen the scope of cryptocurrency use but also accelerate blockchain adoption.
Cross chain, technology on its own has the potential to address scalability issues that have crippled blockchain ecosystem for years. So, it’s a massive boost for blockchain if it can finally pull of interoperability.
If you are just a novice in this regard and want to learn more about blockchain technology then we recommend starting with our free blockchain course. Why not start your blockchain journey now?
Want to know everything about blockchain in detail? Enroll now for blockchain certification and courses.
References
Blockchain Interoperability : Why Is Cross Chain Technology Important?,Diego Geroni,August 13, 2021TPS
Transactions per second (TPS) is computer software and hardware measurement that represents the number of transactions completed in one second by an information system.
Techopedia Explains Transactions Per Second (TPS)
An information system that manipulates business transaction data must have a reliable metric to measure and quantify performance. The transactions per the second measurement are used to calculate the performance of systems that handle routine transactions and record-keeping.
TPS can be calculated with the formula:
T ÷ S = TPS
Where:
T = number of transactions
S = number of seconds
TPS = Transactions per second
The transactions per the second measurement are used by varied organizational departments, including sales, payroll, inventory, shipping, and personnel management.
reference
What Does Transactions Per Second (TPS) Mean?,March 9, 2018The DAO (organization)
The DAO (stylized Đ) was a digital decentralized autonomous organization,[5] and a form of investor-directed venture capital fund.[6] It launched in April 2016 after a crowdfunding campaign via a token sale and it became one of the largest crowdfunding campaigns in history.[6]
The DAO had an objective to provide a new decentralized business model for organizing both commercial and non-profit enterprises.[7][8] It was instantiated on the Ethereum blockchain, and had no conventional management structure or board of directors.[7] The code of the DAO is open-source.[9]
In June 2016, users exploited a vulnerability in The DAO code to enable them to siphon off one-third of The DAO's funds to a subsidiary account. The Ethereum community controversially decided to hard-fork the Ethereum blockchain to restore virtually all funds to the original contract. This split the Ethereum blockchain into two branches, each with its own cryptocurrency, where the original unforked blockchain continued as Ethereum Classic.[10]
By September 2016, the value token of The DAO, known by the moniker DAO, was delisted from major cryptocurrency exchanges (such as Poloniex and Kraken) and had, in effect, become defunct.
History
The open source computer code behind the organization was written principally by Christoph Jentzsch, and released publicly on GitHub, where other contributors added to and modified the code.[6] Simon Jentzsch, Christoph Jentzsch's brother, was also involved in the venture.[6]
The DAO was launched on 30 April 2016 at 01:42:58 AM +UTC on Ethereum Block 1428757,[13] with a website and a 28-day crowdsale to fund the organization.[14] The token sale had raised more than US$34 million by 10 May 2016, and more than US$50 million-worth of Ether (ETH)—the digital value token of the Ethereum network—by 12 May, and over US$100 million by 15 May 2016.[14][15] On 17 May 2016, the largest investor in the DAO held less than 4% of all DAO tokens and the top 100 holders held just over 46% of all DAO tokens.[16] The fund's Ether value as of 21 May 2016 was more than US$150 million,[17] from more than 11,000 investors.[18]
As of May 2016, The DAO had attracted nearly 14% of all ether tokens issued to date.[1]
On 28 May 2016 the DAO tokens became tradable on various cryptocurrency exchanges[19].[11][12]
A paper published in May 2016 noted a number of security vulnerabilities associated with The DAO, and recommended that investors in The DAO hold off from directing The DAO to invest in projects until the problems had been resolved.[20] An Ethereum developer on GitHub pointed out a flaw relating to "recursive calls". On June 9th it was blogged about by Peter Vessenes, founder of the Blockchain Foundation.[21] By June 14, fixes had been proposed and were awaiting approval by members of The DAO.
On June 16th, further attention was called to recursive call vulnerabilities by bloggers affiliated with the Initiative for CryptoCurrencies & Contracts (IC3).[22]
On June 17, 2016, the DAO was subjected to an attack exploiting a combination of vulnerabilities, including the one concerning recursive calls, that resulted in the transfer of 3.6 million Ether - around a third of the 11.5 million Ether that had been committed to The DAO - valued at the time at around $50M.[2][23] The funds were moved into an account subject to a 28-day holding period under the terms of the Ethereum smart contract so were not actually gone.
Members of The DAO and the Ethereum community debated what to do next, with some calling the attack a valid but unethical maneuver, others calling for the Ether to be re-appropriated, and some calling for The DAO to be shut down.[23][24] Eventually[when?], the Ethereum network was hard forked to move the funds in The DAO to a recovery address where they could be exchanged back to Ethereum by their original owners.[25] However, some continued to use the original unforked Ethereum blockchain, now called Ethereum Classic.
In September 2016, Poloniex de-listed DAO trading pairs, followed by Kraken in December 2016.
Operation
The DAO was a decentralized autonomous organization[26] that exists as a set of contracts that resides on the Ethereum blockchain;[27] it did not have a physical address, nor people in formal management roles. The original theory underlying the DAO was that by removing delegated power from directors and placing it directly in the hands of owners the DAO removed the ability of directors and fund managers to misdirect and waste investor funds.[28]
As a blockchain-enabled organization, The DAO claimed to be completely transparent: everything was done by the code, which anyone could see and audit.[29] However, the complexity of the code base and the rapid deployment of the DAO meant that the intended behavior of the organization and its actual behavior differed in serious ways that weren't apparent until after the attack occurred.
The DAO was intended to operate as "a hub that disperses funds (currently in Ether, the Ethereum value token) to projects". Investors received voting rights by means of a digital share token;[26] they vote on proposals that are submitted by "contractors" and a group of volunteers called "curators" check the identity of people submitting proposals and make sure the projects are legal before "whitelisting" them.[6] The profits from the investments will then flow back to its stakeholders.[3]
The DAO did not hold the money of investors; instead, the investors owned DAO tokens that gave them rights to vote on potential projects.[17] Anyone could pull out their funds until the time they first voted.[3]
The DAO's reliance on Ether allowed people to send their money to it from anywhere in the world without providing any identifying information.[17]
In order to provide an interface with real-world legal structures, the founders of The DAO established a Swiss-based company, DAO.Link, registered as a Société à responsabilité limitée (SARL) in Switzerland, apparently co-founded by Slock.it and Neuchatel-based digital currency exchange Bity SA. According to Jentzsch, DAO.Link was in Switzerland because Swiss law allowed it to "take money from an unknown source as long as you know where it's going."
Marketing
In May 2016, TechCrunch described The DAO as "a paradigm shift in the very idea of economic organization. ... It offers complete transparency, total shareholder control, unprecedented flexibility, and autonomous governance."
Risks
In May 2016, the plan called for The DAO to invest Ether in ventures it would back (contractors) and to receive in return "clear payment terms" from contractors. The organizers of the DAO promoted the DAO as providing investors in the DAO a return on their investment via those "clear payment terms" and they warned investors there is "significant risk" that the ventures funded by the DAO may fail.
Risks included unknown attack vectors and programming errors.[27][30] Additional risks noted included the lack of precedence in regulatory and corporate law; how governments and their regulatory agencies would treat The DAO and contracts it made was unknown. There was also a risk that there would be no corporate veil protecting investors from individual legal and financial liability for actions taken by The DAO and by contractors in which The DAO invested. It was unclear if The DAO was selling securities, and if it was, what type of securities those might be.[18]
Additionally, to function in the real world, contractors would likely need to convert the invested Ether into real-world currencies. In May 2016, attorney Andrew Hinkes said that those sales of Ether would be likely to depress the value of Ether.
The code behind The DAO had several safeguards that aimed to prevent its creators or anyone else from mechanically gaming the voting of shareholders to win investments.[17] However, this would not prevent the making of fraudulent profitability projections, and in addition, a paper cited a "number of security vulnerabilities".
Proposals
Slock.it (a German Blockchain venture), and Mobotiq (a French electric vehicle start-up) were listed as seeking potential funding on the daohub.org website during the May "creation period". Both Jentzsch brothers were involved in Slock.it as well.
Regulation
On 25 July 2017, the U.S. Securities and Exchange Commission published a report on initial coin offerings (ICOs) and The DAO, examining "whether The DAO and associated entities and individuals violated federal securities laws with unregistered offers and sales of DAO Tokens in exchange for 'Ether,' a virtual currency." The SEC concluded that DAO tokens sold on the Ethereum blockchain were securities and therefore possible violations of U.S. securities laws.
Decentralized exchange
Decentralized exchanges (DEX) are a type of cryptocurrency exchange which allows for direct peer-to-peer cryptocurrency transactions to take place online securely and without the need for an intermediary.
Overview
In transactions made through decentralized exchanges, the typical third party entities which would normally oversee the security and transfer of assets (e.g. banks, stockbrokers, online payment gateways, government institutions, etc.) are substituted by a blockchain or distributed ledger. Some common methods of operation include the use of smart contracts or order book relaying, although many other variations are possible and with differing degrees of decentralization.
Because traders on a decentralized exchange often do not need to transfer their assets to the exchange before executing a trade, decentralized exchanges reduce the risk of theft from hacking of exchanges,[3][4] but liquidity providers do need to transfer tokens to the decentralized exchange. Decentralized exchanges can also prevent price manipulation or faked trading volume through wash trading, and are more anonymous than exchanges which implement know your customer (KYC) requirements.
There are some signs that decentralized exchanges have been suffering from low trading volumes and market liquidity.[5] The 0x project, a protocol for building decentralized exchanges with interchangeable liquidity attempts to solve this issue.
Drawbacks
Due to a lack of KYC process, and no way to revert a transaction, users are at a loss if they are ever hacked for their passwords or private keys.[7]
Although liquidity pool DEX are the most widely used, they may have some drawbacks. The most common problems of liquidity pool DEXes are price slippage and front running.
Price slippage occurs because of the AMM (Automated Market Makers) nature itself — the larger the deal, the stronger impact it has on the price. For example, if the constant product AMM is in use, every deal must keep the product xy = k constant, where x and y are quantities of two cryptocurrencies (or tokens) in the pool. So the larger is the input amount Δx, the lower is the final ratio y / x that gives an exchange price. The problem is mostly significant for large deals or small liquidity pools.
Front running is a special type of attack in public blockchains when some participant (usually a miner) seeing an upcoming trading transaction puts his own transaction ahead (playing with a transaction fee for example), making the initial transaction less profitable or even reverted.
Ideas of improving front running resistance of the constant product AMM were first discussed in a post by Vitalik Buterin.
Degrees of decentralization
A decentralized exchange can still have centralized components, whereby some control of the exchange is still in the hands of a central authority. A notable example being IDEX blocking New York State users from placing orders on the platform.
In July 2018, decentralized exchange Bancor was reportedly hacked and suffered a loss of $13.5M in assets before freezing funds.[10] In a Tweet, Charlie Lee, the creator of Litecoin spoke out and claimed an exchange cannot be decentralized if it can lose or freeze customer funds.
Operators of decentralized exchanges can face legal consequences from government regulators. One example is the founder of EtherDelta, who in November 2018 settled charges with the U.S. Securities and Exchange Commission over operating an unregistered securities exchange.
Uniswap, which is built upon the Ethereum blockchain, has the largest trading volume of any DEX.[13] It deployed its V3 to the Ethereum mainnet on May 5th 2021.
Bitcoin
Bitcoin (₿) is a decentralized digital currency, without a central bank or single administrator, that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries.[7] Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. The cryptocurrency was invented in 2008 by an unknown person or group of people using the name Satoshi Nakamoto.[9] The currency began use in 2009[10] when its implementation was released as open-source software.
Bitcoins are created as a reward for a process known as mining. They can be exchanged for other currencies, products, and services. Bitcoin has been criticized for its use in illegal transactions, the large amount of electricity (and thus carbon footprint) used by mining, price volatility, and thefts from exchanges. Some investors and economists have characterized it as a speculative bubble at various times. Others have used it as an investment, although several regulatory agencies have issued investor alerts about bitcoin.[11][12][13] In September 2021, El Salvador officially adopted Bitcoin as legal tender, becoming the first nation to do so.
The word bitcoin was defined in a white paper published on 31 October 2008.[4][15] It is a compound of the words bit and coin.[16] No uniform convention for bitcoin capitalization exists; some sources use Bitcoin, capitalized, to refer to the technology and network and bitcoin, lowercase, for the unit of account.[17] The Wall Street Journal,[18] The Chronicle of Higher Education,[19] and the Oxford English Dictionary[16] advocate the use of lowercase bitcoin in all cases.
Design
Units and divisibility
The unit of account of the bitcoin system is the bitcoin. Currency codes for representing bitcoin are BTC[a] and XBT.[b][23]: 2 Its Unicode character is ₿.[1] One bitcoin is divisible to eight decimal places.[6]: ch. 5 Units for smaller amounts of bitcoin are the millibitcoin (mBTC), equal to 1⁄1000 bitcoin, and the satoshi (sat), which is the smallest possible division, and named in homage to bitcoin's creator, representing 1⁄100000000 (one hundred millionth) bitcoin.[2] 100,000 satoshis are one mBTC.
Blockchain
The bitcoin blockchain is a public ledger that records bitcoin transactions.[27] It is implemented as a chain of blocks, each block containing a hash of the previous block up to the genesis block[c] in the chain. A network of communicating nodes running bitcoin software maintains the blockchain.[28]: 215–219 Transactions of the form payer X sends Y bitcoins to payee Z are broadcast to this network using readily available software applications.
Network nodes can validate transactions, add them to their copy of the ledger, and then broadcast these ledger additions to other nodes. To achieve independent verification of the chain of ownership each network node stores its own copy of the blockchain.[29] At varying intervals of time averaging to every 10 minutes, a new group of accepted transactions, called a block, is created, added to the blockchain, and quickly published to all nodes, without requiring central oversight. This allows bitcoin software to determine when a particular bitcoin was spent, which is needed to prevent double-spending. A conventional ledger records the transfers of actual bills or promissory notes that exist apart from it, but the blockchain is the only place that bitcoins can be said to exist in the form of unspent outputs of transactions.
Individual blocks, public addresses and transactions within blocks can be examined using a blockchain explorer.
Transactions
Transactions are defined using a Forth-like scripting language.[6]: ch. 5 Transactions consist of one or more inputs and one or more outputs. When a user sends bitcoins, the user designates each address and the amount of bitcoin being sent to that address in an output. To prevent double spending, each input must refer to a previous unspent output in the blockchain.[30] The use of multiple inputs corresponds to the use of multiple coins in a cash transaction. Since transactions can have multiple outputs, users can send bitcoins to multiple recipients in one transaction. As in a cash transaction, the sum of inputs (coins used to pay) can exceed the intended sum of payments. In such a case, an additional output is used, returning the change back to the payer.[30] Any input satoshis not accounted for in the transaction outputs become the transaction fee.
Though transaction fees are optional, miners can choose which transactions to process and prioritize those that pay higher fees.[30] Miners may choose transactions based on the fee paid relative to their storage size, not the absolute amount of money paid as a fee. These fees are generally measured in satoshis per byte (sat/b). The size of transactions is dependent on the number of inputs used to create the transaction, and the number of outputs.
The blocks in the blockchain were originally limited to 32 megabytes in size. The block size limit of one megabyte was introduced by Satoshi Nakamoto in 2010. Eventually the block size limit of one megabyte created problems for transaction processing, such as increasing transaction fees and delayed processing of transactions.[31] Andreas Antonopoulos has stated Lightning Network is a potential scaling solution and referred to lightning as a second layer routing network.
Ownership
In the blockchain, bitcoins are registered to bitcoin addresses. Creating a bitcoin address requires nothing more than picking a random valid private key and computing the corresponding bitcoin address. This computation can be done in a split second. But the reverse, computing the private key of a given bitcoin address, is practically unfeasible.[6]: ch. 4 Users can tell others or make public a bitcoin address without compromising its corresponding private key. Moreover, the number of valid private keys is so vast that it is extremely unlikely someone will compute a key-pair that is already in use and has funds. The vast number of valid private keys makes it unfeasible that brute force could be used to compromise a private key. To be able to spend their bitcoins, the owner must know the corresponding private key and digitally sign the transaction.[d] The network verifies the signature using the public key; the private key is never revealed.
If the private key is lost, the bitcoin network will not recognize any other evidence of ownership;[28] the coins are then unusable, and effectively lost. For example, in 2013 one user claimed to have lost 7,500 bitcoins, worth $7.5 million at the time, when he accidentally discarded a hard drive containing his private key.[34] About 20% of all bitcoins are believed to be lost -they would have had a market value of about $20 billion at July 2018 prices.
To ensure the security of bitcoins, the private key must be kept secret.[6]: ch. 10 If the private key is revealed to a third party, e.g. through a data breach, the third party can use it to steal any associated bitcoins.[36] As of December 2017, around 980,000 bitcoins have been stolen from cryptocurrency exchanges.
Regarding ownership distribution, as of 16 March 2018, 0.5% of bitcoin wallets own 87% of all bitcoins ever mined.[38]
Mining
Mining is a record-keeping service done through the use of computer processing power.[f] Miners keep the blockchain consistent, complete, and unalterable by repeatedly grouping newly broadcast transactions into a block, which is then broadcast to the network and verified by recipient nodes.[27] Each block contains a SHA-256 cryptographic hash of the previous block,[27] thus linking it to the previous block and giving the blockchain its name.
To be accepted by the rest of the network, a new block must contain a proof-of-work (PoW).[27][g] The PoW requires miners to find a number called a nonce (number used once), such that when the block content is hashed along with the nonce, the result is numerically smaller than the network's difficulty target.[6]: ch. 8 This proof is easy for any node in the network to verify, but extremely time-consuming to generate, as for a secure cryptographic hash, miners must try many different nonce values (usually the sequence of tested values is the ascending natural numbers: 0, 1, 2, 3, ...) before a result happens to be less than the difficulty target. Because the difficulty target is extremely small compared to a typical SHA-256 hash, block hashes have many leading zeros[6]: ch. 8 as can be seen in this example block hash:
0000000000000000000590fc0f3eba193a278534220b2b37e9849e1a770ca959
By adjusting this difficulty target, the amount of work needed to generate a block can be changed. Every 2,016 blocks (approximately 14 days given roughly 10 minutes per block), nodes deterministically adjust the difficulty target based on the recent rate of block generation, with the aim of keeping the average time between new blocks at ten minutes. In this way the system automatically adapts to the total amount of mining power on the network.[6]: ch. 8 As of September 2021, it takes on average 79 sextillion (79 thousand billion billion) attempts to generate a block hash smaller than the difficulty target.[43] Computations of this magnitude are extremely expensive and utilize specialized hardware.
The proof-of-work system, alongside the chaining of blocks, makes modifications of the blockchain extremely hard, as an attacker must modify all subsequent blocks in order for the modifications of one block to be accepted.[45] As new blocks are mined all the time, the difficulty of modifying a block increases as time passes and the number of subsequent blocks (also called confirmations of the given block) increases.
Computing power is often bundled together by a Mining pool to reduce variance in miner income. Individual mining rigs often have to wait for long periods to confirm a block of transactions and receive payment. In a pool, all participating miners get paid every time a participating server solves a block. This payment depends on the amount of work an individual miner contributed to help find that block.[46]
Supply
The successful miner finding the new block is allowed by the rest of the network to collect for themselves all transaction fees from transactions they included in the block, as well as a pre-determined reward of newly created bitcoins.[47] As of 11 May 2020, this reward is currently 6.25 newly created bitcoins per block.[48] To claim this reward, a special transaction called a coinbase is included in the block, with the miner as the payee.[6]: ch. 8 All bitcoins in existence have been created through this type of transaction. The bitcoin protocol specifies that the reward for adding a block will be reduced by half every 210,000 blocks (approximately every four years). Eventually, the reward will round down to zero, and the limit of 21 million bitcoins[h] will be reached c. 2140; the record keeping will then be rewarded by transaction fees only.
Decentralization
Bitcoin is decentralized thus:
- Bitcoin does not have a central authority.
- he bitcoin network is peer-to-peer,[10] without central servers.
- The network also has no central storage; the bitcoin ledger is distributed.
- The ledger is public; anybody can store it on a computer.
- There is no single administrator;[7] the ledger is maintained by a network of equally privileged miners.
- Anyone can become a miner.
- The additions to the ledger are maintained through competition. Until a new block is added to the ledger, it is not known which miner will create the block.
- The issuance of bitcoins is decentralized. They are issued as a reward for the creation of a new block.
- Anybody can create a new bitcoin address (a bitcoin counterpart of a bank account) without needing any approval.
- Anybody can send a transaction to the network without needing any approval; the network merely confirms that the transaction is legitimate.
Conversely, researchers have pointed out at a "trend towards centralization". Although bitcoin can be sent directly from user to user, in practice intermediaries are widely used.[28]: 220–222 Bitcoin miners join large mining pools to minimize the variance of their income.[28]: 215, 219–222 [52]: 3 [53] Because transactions on the network are confirmed by miners, decentralization of the network requires that no single miner or mining pool obtains 51% of the hashing power, which would allow them to double-spend coins, prevent certain transactions from being verified and prevent other miners from earning income.[54] As of 2013 just six mining pools controlled 75% of overall bitcoin hashing power.[54] In 2014 mining pool Ghash.io obtained 51% hashing power which raised significant controversies about the safety of the network. The pool has voluntarily capped their hashing power at 39.99% and requested other pools to act responsibly for the benefit of the whole network.[55] Around the year 2017, over 70% of the hashing power and 90% of transactions were operating from China.
According to researchers, other parts of the ecosystem are also "controlled by a small set of entities", notably the maintenance of the client software, online wallets and simplified payment verification (SPV) clients.
Privacy and fungibility
Bitcoin is pseudonymous, meaning that funds are not tied to real-world entities but rather bitcoin addresses. Owners of bitcoin addresses are not explicitly identified, but all transactions on the blockchain are public. In addition, transactions can be linked to individuals and companies through "idioms of use" (e.g., transactions that spend coins from multiple inputs indicate that the inputs may have a common owner) and corroborating public transaction data with known information on owners of certain addresses.[57] Additionally, bitcoin exchanges, where bitcoins are traded for traditional currencies, may be required by law to collect personal information.[58] To heighten financial privacy, a new bitcoin address can be generated for each transaction.
Wallets and similar software technically handle all bitcoins as equivalent, establishing the basic level of fungibility. Researchers have pointed out that the history of each bitcoin is registered and publicly available in the blockchain ledger, and that some users may refuse to accept bitcoins coming from controversial transactions, which would harm bitcoin's fungibility.[60] For example, in 2012, Mt. Gox froze accounts of users who deposited bitcoins that were known to have just been stolen.
Wallets
A wallet stores the information necessary to transact bitcoins. While wallets are often described as a place to hold[62] or store bitcoins, due to the nature of the system, bitcoins are inseparable from the blockchain transaction ledger. A wallet is more correctly defined as something that "stores the digital credentials for your bitcoin holdings" and allows one to access (and spend) them.[6]: ch. 1, glossary Bitcoin uses public-key cryptography, in which two cryptographic keys, one public and one private, are generated.[63] At its most basic, a wallet is a collection of these keys.
Software wallets
The first wallet program, simply named Bitcoin, and sometimes referred to as the Satoshi client, was released in 2009 by Satoshi Nakamoto as open-source software.[10] In version 0.5 the client moved from the wxWidgets user interface toolkit to Qt, and the whole bundle was referred to as Bitcoin-Qt.[64] After the release of version 0.9, the software bundle was renamed Bitcoin Core to distinguish itself from the underlying network.[65][66] Bitcoin Core is, perhaps, the best known implementation or client. Alternative clients (forks of Bitcoin Core) exist, such as Bitcoin XT, Bitcoin Unlimited,[67] and Parity Bitcoin.
There are several modes which wallets can operate in. They have an inverse relationship with regards to trustlessness and computational requirements.
- Full clients verify transactions directly by downloading a full copy of the blockchain (over 150 GB as of January 2018).[69] They are the most secure and reliable way of using the network, as trust in external parties is not required. Full clients check the validity of mined blocks, preventing them from transacting on a chain that breaks or alters network rules. Because of its size and complexity, downloading and verifying the entire blockchain is not suitable for all computing devices.
- Lightweight clients consult full nodes to send and receive transactions without requiring a local copy of the entire blockchain (see simplified payment verification – SPV). This makes lightweight clients much faster to set up and allows them to be used on low-power, low-bandwidth devices such as smartphones. When using a lightweight wallet, however, the user must trust full nodes, as it can report faulty values back to the user. Lightweight clients follow the longest blockchain and do not ensure it is valid, requiring trust in full nodes.
Third-party internet services called online wallets or webwallets offer similar functionality but may be easier to use. In this case, credentials to access funds are stored with the online wallet provider rather than on the user's hardware.[71] As a result, the user must have complete trust in the online wallet provider. A malicious provider or a breach in server security may cause entrusted bitcoins to be stolen. An example of such a security breach occurred with Mt. Gox in 2011.
Cold storage
Wallet software is targeted by hackers because of the lucrative potential for stealing bitcoins.[36] A technique called "cold storage" keeps private keys out of reach of hackers; this is accomplished by keeping private keys offline at all times[73][6]: ch. 4 by generating them on a device that is not connected to the internet.[74]: 39 The credentials necessary to spend bitcoins can be stored offline in a number of different ways, from specialized hardware wallets to simple paper printouts of the private key.
Hardware wallets
A hardware wallet is a computer peripheral that signs transactions as requested by the user. These devices store private keys and carry out signing and encryption internally,[73] and do not share any sensitive information with the host computer except already signed (and thus unalterable) transactions.[75] Because hardware wallets never expose their private keys, even computers that may be compromised by malware do not have a vector to access or steal them.
The user sets a passcode when setting up a hardware wallet.[73] As hardware wallets are tamper-resistant, the passcode will be needed to extract any money.
History
Creation
The domain name bitcoin.org was registered on 18 August 2008.[80] On 31 October 2008, a link to a paper authored by Satoshi Nakamoto titled Bitcoin: A Peer-to-Peer Electronic Cash System[4] was posted to a cryptography mailing list.[81] Nakamoto implemented the bitcoin software as open-source code and released it in January 2009.[82][83][10] Nakamoto's identity remains unknown.
On 3 January 2009, the bitcoin network was created when Nakamoto mined the starting block of the chain, known as the genesis block.[84][85] Embedded in the coinbase of this block was the text "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks".[10] This note references a headline published by The Times and has been interpreted as both a timestamp and a comment on the instability caused by fractional-reserve banking.
The receiver of the first bitcoin transaction was Hal Finney, who had created the first reusable proof-of-work system (RPoW) in 2004.[87] Finney downloaded the bitcoin software on its release date, and on 12 January 2009 received ten bitcoins from Nakamoto.[88][89] Other early cypherpunk supporters were creators of bitcoin predecessors: Wei Dai, creator of b-money, and Nick Szabo, creator of bit gold.[84] In 2010, the first known commercial transaction using bitcoin occurred when programmer Laszlo Hanyecz bought two Papa John's pizzas for ₿10,000 from Jeremy Sturdivant.
Blockchain analysts estimate that Nakamoto had mined about one million bitcoins[95] before disappearing in 2010 when he handed the network alert key and control of the code repository over to Gavin Andresen. Andresen later became lead developer at the Bitcoin Foundation.[96][97] Andresen then sought to decentralize control. This left opportunity for controversy to develop over the future development path of bitcoin, in contrast to the perceived authority of Nakamoto's contributions.
2011–2012
After early "proof-of-concept" transactions, the first major users of bitcoin were black markets, such as Silk Road. During its 30 months of existence, beginning in February 2011, Silk Road exclusively accepted bitcoins as payment, transacting 9.9 million in bitcoins, worth about $214 million.
In 2011, the price started at $0.30 per bitcoin, growing to $5.27 for the year. The price rose to $31.50 on 8 June. Within a month, the price fell to $11.00. The next month it fell to $7.80, and in another month to $4.77.
In 2012, bitcoin prices started at $5.27, growing to $13.30 for the year.[98] By 9 January the price had risen to $7.38, but then crashed by 49% to $3.80 over the next 16 days. The price then rose to $16.41 on 17 August, but fell by 57% to $7.10 over the next three days.
The Bitcoin Foundation was founded in September 2012 to promote bitcoin's development and uptake.
On 1 November 2011, the reference implementation Bitcoin-Qt version 0.5.0 was released. It introduced a front end that used the Qt user interface toolkit.[101] The software previously used Berkeley DB for database management. Developers switched to LevelDB in release 0.8 in order to reduce blockchain synchronization time.[citation needed] The update to this release resulted in a minor blockchain fork on 11 March 2013. The fork was resolved shortly afterwards.[citation needed] Seeding nodes through IRC was discontinued in version 0.8.2. From version 0.9.0 the software was renamed to Bitcoin Core. Transaction fees were reduced again by a factor of ten as a means to encourage microtransactions.[citation needed] Although Bitcoin Core does not use OpenSSL for the operation of the network, the software did use OpenSSL for remote procedure calls. Version 0.9.1 was released to remove the network's vulnerability to the Heartbleed bug.
2013–2016
In 2013, prices started at $13.30 rising to $770 by 1 January 2014.
In March 2013 the blockchain temporarily split into two independent chains with different rules due to a bug in version 0.8 of the bitcoin software. The two blockchains operated simultaneously for six hours, each with its own version of the transaction history from the moment of the split. Normal operation was restored when the majority of the network downgraded to version 0.7 of the bitcoin software, selecting the backwards-compatible version of the blockchain. As a result, this blockchain became the longest chain and could be accepted by all participants, regardless of their bitcoin software version.[102] During the split, the Mt. Gox exchange briefly halted bitcoin deposits and the price dropped by 23% to $37[102][103] before recovering to the previous level of approximately $48 in the following hours.
The US Financial Crimes Enforcement Network (FinCEN) established regulatory guidelines for "decentralized virtual currencies" such as bitcoin, classifying American bitcoin miners who sell their generated bitcoins as Money Service Businesses (MSBs), that are subject to registration or other legal obligations.
In April, exchanges BitInstant and Mt. Gox experienced processing delays due to insufficient capacity[108] resulting in the bitcoin price dropping from $266 to $76 before returning to $160 within six hours.[109] The bitcoin price rose to $259 on 10 April, but then crashed by 83% to $45 over the next three days.
On 15 May 2013, US authorities seized accounts associated with Mt. Gox after discovering it had not registered as a money transmitter with FinCEN in the US.[110][111] On 23 June 2013, the US Drug Enforcement Administration listed ₿11.02 as a seized asset in a United States Department of Justice seizure notice pursuant to 21 U.S.C. § 881. This marked the first time a government agency had seized bitcoin.[112] The FBI seized about ₿30,000[113] in October 2013 from the dark web website Silk Road, following the arrest of Ross William Ulbricht.[114][115][116] These bitcoins were sold at blind auction by the United States Marshals Service to venture capital investor Tim Draper.[113] Bitcoin's price rose to $755 on 19 November and crashed by 50% to $378 the same day. On 30 November 2013, the price reached $1,163 before starting a long-term crash, declining by 87% to $152 in January 2015.
On 5 December 2013, the People's Bank of China prohibited Chinese financial institutions from using bitcoins.[117] After the announcement, the value of bitcoins dropped,[118] and Baidu no longer accepted bitcoins for certain services.[119] Buying real-world goods with any virtual currency had been illegal in China since at least 2009.
In 2014, prices started at $770 and fell to $314 for the year.[98] On 30 July 2014, the Wikimedia Foundation started accepting donations of bitcoin.
In 2015, prices started at $314 and rose to $434 for the year. In 2016, prices rose and climbed up to $998 by 1 January 2017.
Release 0.10 of the software was made public on 16 February 2015. It introduced a consensus library which gave programmers easy access to the rules governing consensus on the network. In version 0.11.2 developers added a new feature which allowed transactions to be made unspendable until a specific time in the future.[122] Bitcoin Core 0.12.1 was released on 15 April 2016, and enabled multiple soft forks to occur concurrently.[123] Around 100 contributors worked on Bitcoin Core 0.13.0 which was released on 23 August 2016.
In July 2016, the CheckSequenceVerify soft fork activated.
In October 2016, Bitcoin Core's 0.13.1 release featured the "Segwit" soft fork that included a scaling improvement aiming to optimize the bitcoin blocksize.[citation needed] The patch which was originally finalised in April, and 35 developers were engaged to deploy it.[citation needed] This release featured Segregated Witness (SegWit) which aimed to place downward pressure on transaction fees as well as increase the maximum transaction capacity of the network.[125][non-primary source needed] The 0.13.1 release endured extensive testing and research leading to some delays in its release date.[citation needed] SegWit prevents various forms of transaction malleability.
2017–2019
Research produced by the University of Cambridge estimated that in 2017, there were 2.9 to 5.8 million unique users using a cryptocurrency wallet, most of them using bitcoin.[127] On 15 July 2017, the controversial Segregated Witness [SegWit] software upgrade was approved ("locked-in"). Segwit was intended to support the Lightning Network as well as improve scalability.[128] SegWit was subsequently activated on the network on 24 August 2017. The bitcoin price rose almost 50% in the week following SegWit's approval.[128] On 21 July 2017, bitcoin was trading at $2,748, up 52% from 14 July 2017's $1,835.[128] Supporters of large blocks who were dissatisfied with the activation of SegWit forked the software on 1 August 2017 to create Bitcoin Cash, becoming one of many forks of bitcoin such as Bitcoin Gold.
Prices started at $998 in 2017 and rose to $13,412.44 on 1 January 2018,[98] after reaching its all-time high of $19,783.06 on 17 December 2017.
China banned trading in bitcoin, with first steps taken in September 2017, and a complete ban that started on 1 February 2018. Bitcoin prices then fell from $9,052 to $6,914 on 5 February 2018.[99] The percentage of bitcoin trading in the Chinese renminbi fell from over 90% in September 2017 to less than 1% in June 2018.
Throughout the rest of the first half of 2018, bitcoin's price fluctuated between $11,480 and $5,848. On 1 July 2018, bitcoin's price was $6,343.[132][133] The price on 1 January 2019 was $3,747, down 72% for 2018 and down 81% since the all-time high.
In September 2018, an anonymous party discovered and reported an invalid-block denial-of-server vulnerability to developers of Bitcoin Core, Bitcoin ABC and Bitcoin Unlimited. Further analysis by bitcoin developers showed the issue could also allow the creation of blocks violating the 21 million coin limit and CVE-2018-17144 was assigned and the issue resolved.
Bitcoin prices were negatively affected by several hacks or thefts from cryptocurrency exchanges, including thefts from Coincheck in January 2018, Bithumb in June, and Bancor in July. For the first six months of 2018, $761 million worth of cryptocurrencies was reported stolen from exchanges.[136] Bitcoin's price was affected even though other cryptocurrencies were stolen at Coinrail and Bancor as investors worried about the security of cryptocurrency exchanges.[137][138][139] In September 2019 the Intercontinental Exchange (the owner of the NYSE) began trading of bitcoin futures on its exchange called Bakkt.[140] Bakkt also announced that it would launch options on bitcoin in December 2019.[141] In December 2019, YouTube removed bitcoin and cryptocurrency videos, but later restored the content after judging they had "made the wrong call."
In February 2019, Canadian cryptocurrency exchange Quadriga Fintech Solutions failed with approximately $200 million missing.[143] By June 2019 the price had recovered to $13,000.
2020–present
On 13 March 2020, bitcoin fell below $4,000 during a broad market selloff, after trading above $10,000 in February 2020.[145] On 11 March 2020, 281,000 bitcoins were sold, held by owners for only thirty days.[144] This compared to ₿4,131 that had laid dormant for a year or more, indicating that the vast majority of the bitcoin volatility on that day was from recent buyers. During the week of 11 March 2020, cryptocurrency exchange Kraken experienced an 83% increase in the number of account signups over the week of bitcoin's price collapse, a result of buyers looking to capitalize on the low price.[144] These events were attributed to the onset of the COVID-19 pandemic.
In August 2020, MicroStrategy invested $250 million in bitcoin as a treasury reserve asset.[146] In October 2020, Square, Inc. placed approximately 1% of total assets ($50 million) in bitcoin.[147] In November 2020, PayPal announced that US users could buy, hold, or sell bitcoin.[148] On 30 November 2020, the bitcoin value reached a new all-time high of $19,860, topping the previous high of December 2017.[149] Alexander Vinnik, founder of BTC-e, was convicted and sentenced to five years in prison for money laundering in France while refusing to testify during his trial.[150] In December 2020 Massachusetts Mutual Life Insurance Company announced a bitcoin purchase of US$100 million, or roughly 0.04% of its general investment account.
On 19 January 2021, Elon Musk placed the handle #Bitcoin in his Twitter profile, tweeting "In retrospect, it was inevitable", which caused the price to briefly rise about $5000 in an hour to $37,299.[152] On 25 January 2021, Microstrategy announced that it continued to buy bitcoin and as of the same date it had holdings of ₿70,784 worth $2.38 billion.[153] On 8 February 2021 Tesla's announcement of a bitcoin purchase of US$1.5 billion and the plan to start accepting bitcoin as payment for vehicles, pushed the bitcoin price to $44,141.[154] On 18 February 2021, Elon Musk stated that "owning bitcoin was only a little better than holding conventional cash, but that the slight difference made it a better asset to hold".[155] After 49 days of accepting the digital currency, Tesla reversed course on 12 May 2021, saying they would no longer take Bitcoin due to concerns that "mining" the cryptocurrency was contributing to the consumption of fossil fuels and climate change.[156] The decision resulted in the price of Bitcoin dropping around 12% on 13 May.[157] During a July Bitcoin conference, Musk suggested Tesla could possibly help Bitcoin miners switch to renewable energy in the future and also stated at the same conference that if Bitcoin mining reaches, and trends above 50 percent renewable energy usage, that "Tesla would resume accepting bitcoin." The price for bitcoin rose after this announcement.
In September 2020, the Canton of Zug, Switzerland, announced to start to accepting tax payments in bitcoin by February 2021.
In June 2021, the Legislative Assembly of El Salvador voted legislation to make Bitcoin legal tender in El Salvador.[j][169][164][170] The law took effect on 7 September.[171][8] The implementation of the law has been met with protests[172] and calls to make the currency optional, not compulsory.[173] According to a survey by the Central American University, the majority of Salvadorans disagreed with using cryptocurrency as a legal tender,[174][175] and a survey by the Center for Citizen Studies (CEC) showed that 91% of the country prefers the dollar over Bitcoin.[176] As of October 2021, the country's government was exploring mining bitcoin with geothermal power and issuing bonds tied to bitcoin.[177] According to a survey done by the Central American University 100 days after the Bitcoin Law came into force: 34.8% of the population has no confidence in Bitcoin, 35.3% has little confidence, 13.2% has some confidence, and 14.1% has a lot of confidence. 56.6% of respondents have downloaded the government Bitcoin wallet; among them 62.9% has never used it or only once whereas 36.3% uses Bitcoin at least once a month.
Also In June, the Taproot network software upgrade was approved, adding support for Schnorr signatures, improved functionality of Smart contracts and Lightning Network.[180] The upgrade was installed in November.
On 16 October 2021, the SEC approved the ProShares Bitcoin Strategy ETF, a cash-settled futures exchange-traded fund (ETF). The first bitcoin ETF in the United States gained 5% on its first trading day on 19 October 2021.
Associated ideologies
Satoshi Nakamoto stated in his white paper that: "The root problem with conventional currencies is all the trust that's required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust.
Austrian economics roots
According to the European Central Bank, the decentralization of money offered by bitcoin has its theoretical roots in the Austrian school of economics, especially with Friedrich von Hayek in his book Denationalisation of Money: The Argument Refined,[185] in which Hayek advocates a complete free market in the production, distribution and management of money to end the monopoly of central banks.
Anarchism and libertarianism
According to The New York Times, libertarians and anarchists were attracted to the philosophical idea behind bitcoin. Early bitcoin supporter Roger Ver said: "At first, almost everyone who got involved did so for philosophical reasons. We saw bitcoin as a great idea, as a way to separate money from the state."[184] The Economist describes bitcoin as "a techno-anarchist project to create an online version of cash, a way for people to transact without the possibility of interference from malicious governments or banks".[187] Economist Paul Krugman argues that cryptocurrencies like bitcoin are "something of a cult" based in "paranoid fantasies" of government power.
External video
video icon The Declaration Of Bitcoin's Independence, BraveTheWorld, 4:38[189]
Nigel Dodd argues in The Social Life of Bitcoin that the essence of the bitcoin ideology is to remove money from social, as well as governmental, control.[190] Dodd quotes a YouTube video, with Roger Ver, Jeff Berwick, Charlie Shrem, Andreas Antonopoulos, Gavin Wood, Trace Meyer and other proponents of bitcoin reading The Declaration of Bitcoin's Independence. The declaration includes a message of crypto-anarchism with the words: "Bitcoin is inherently anti-establishment, anti-system, and anti-state. Bitcoin undermines governments and disrupts institutions because bitcoin is fundamentally humanitarian."[190][189]
David Golumbia says that the ideas influencing bitcoin advocates emerge from right-wing extremist movements such as the Liberty Lobby and the John Birch Society and their anti-Central Bank rhetoric, or, more recently, Ron Paul and Tea Party-style libertarianism.[191] Steve Bannon, who owns a "good stake" in bitcoin, considers it to be "disruptive populism. It takes control back from central authorities. It's revolutionary."[192]
A 2014 study of Google Trends data found correlations between bitcoin-related searches and ones related to computer programming and illegal activity, but not libertarianism or investment topics.
Economics
Bitcoin is a digital asset designed to work in peer-to-peer transactions as a currency.[4][194] Bitcoins have three qualities useful in a currency, according to The Economist in January 2015: they are "hard to earn, limited in supply and easy to verify."[195] Per some researchers, as of 2015, bitcoin functions more as a payment system than as a currency.[28]
Economists define money as serving the following three purposes: a store of value, a medium of exchange, and a unit of account.[196] According to The Economist in 2014, bitcoin functions best as a medium of exchange.[196] However, this is debated, and a 2018 assessment by The Economist stated that cryptocurrencies met none of these three criteria.[187] Yale economist Robert J. Shiller writes that bitcoin has potential as a unit of account for measuring the relative value of goods, as with Chile's Unidad de Fomento, but that "Bitcoin in its present form [...] doesn't really solve any sensible economic problem".[197]
According to research by Cambridge University, between 2.9 million and 5.8 million unique users used a cryptocurrency wallet in 2017, most of them for bitcoin. The number of users has grown significantly since 2013, when there were 300,000–1.3 million users.
Acceptance by merchants
The overwhelming majority of bitcoin transactions take place on a cryptocurrency exchange, rather than being used in transactions with merchants.[198] Delays processing payments through the blockchain of about ten minutes make bitcoin use very difficult in a retail setting. Prices are not usually quoted in units of bitcoin and many trades involve one, or sometimes two, conversions into conventional currencies.[28] Merchants that do accept bitcoin payments may use payment service providers to perform the conversions.[199]
In 2017 and 2018 bitcoin's acceptance among major online retailers included only three of the top 500 U.S. online merchants, down from five in 2016.[198] Reasons for this decline include high transaction fees due to bitcoin's scalability issues and long transaction times.[200]
Bloomberg reported that the largest 17 crypto merchant-processing services handled $69 million in June 2018, down from $411 million in September 2017. Bitcoin is "not actually usable" for retail transactions because of high costs and the inability to process chargebacks, according to Nicholas Weaver, a researcher quoted by Bloomberg. High price volatility and transaction fees make paying for small retail purchases with bitcoin impractical, according to economist Kim Grauer. However, bitcoin continues to be used for large-item purchases on sites such as Overstock.com, and for cross-border payments to freelancers and other vendors.
Financial institutions
Bitcoins can be bought on digital currency exchanges.
Per researchers, "there is little sign of bitcoin use" in international remittances despite high fees charged by banks and Western Union who compete in this market.[28] The South China Morning Post, however, mentions the use of bitcoin by Hong Kong workers to transfer money home.[202]
In 2014, the National Australia Bank closed accounts of businesses with ties to bitcoin,[203] and HSBC refused to serve a hedge fund with links to bitcoin.[204] Australian banks in general have been reported as closing down bank accounts of operators of businesses involving the currency.[205]
On 10 December 2017, the Chicago Board Options Exchange started trading bitcoin futures,[206] followed by the Chicago Mercantile Exchange, which started trading bitcoin futures on 17 December 2017.[207]
In September 2019 the Central Bank of Venezuela, at the request of PDVSA, ran tests to determine if bitcoin and ether could be held in central bank's reserves. The request was motivated by oil company's goal to pay its suppliers.
As an investment
The Winklevoss twins have purchased bitcoin. In 2013, The Washington Post reported a claim that they owned 1% of all the bitcoins in existence at the time.[209]
Other methods of investment are bitcoin funds. The first regulated bitcoin fund was established in Jersey in July 2014 and approved by the Jersey Financial Services Commission.[210]
Forbes named bitcoin the best investment of 2013.[211] In 2014, Bloomberg named bitcoin one of its worst investments of the year.[212] In 2015, bitcoin topped Bloomberg's currency tables.[213]
According to bitinfocharts.com, in 2017, there were 9,272 bitcoin wallets with more than $1 million worth of bitcoins.[214] The exact number of bitcoin millionaires is uncertain as a single person can have more than one bitcoin wallet.
Price and volatility
The price of bitcoins has gone through cycles of appreciation and depreciation referred to by some as bubbles and busts.[220] In 2011, the value of one bitcoin rapidly rose from about US$0.30 to US$32 before returning to US$2.[221] In the latter half of 2012 and during the 2012–13 Cypriot financial crisis, the bitcoin price began to rise,[222] reaching a high of US$266 on 10 April 2013, before crashing to around US$50. On 29 November 2013, the cost of one bitcoin rose to a peak of US$1,242.[223] In 2014, the price fell sharply, and as of April remained depressed at little more than half 2013 prices. As of August 2014 it was under US$600.[224]
According to Mark T. Williams, as of 30 September 2014, bitcoin has volatility seven times greater than gold, eight times greater than the S&P 500, and 18 times greater than the US dollar.[225] Hodl is a meme created in reference to holding (as opposed to selling) during periods of volatility. Unusual for an asset, bitcoin weekend trading during December 2020 was higher than for weekdays.[226] Hedge funds (using high leverage and derivates)[227] have attempted to use the volatility to profit from downward price movements. At the end of January 2021, such positions were over $1 billion, their highest of all time.[228] As of 8 February 2021, the closing price of bitcoin equaled US$44,797.[229]
Legal status, tax and regulation
Because of bitcoin's decentralized nature and its trading on online exchanges located in many countries, regulation of bitcoin has been difficult. However, the use of bitcoin can be criminalized, and shutting down exchanges and the peer-to-peer economy in a given country would constitute a de facto ban.[230] The legal status of bitcoin varies substantially from country to country and is still undefined or changing in many of them. Regulations and bans that apply to bitcoin probably extend to similar cryptocurrency systems.[219]
According to the Library of Congress, an "absolute ban" on trading or using cryptocurrencies applies in nine countries: Algeria, Bolivia, Egypt, Iraq, Morocco, Nepal, Pakistan, Vietnam, and the United Arab Emirates. An "implicit ban" applies in another 15 countries, which include Bahrain, Bangladesh, China, Colombia, the Dominican Republic, Indonesia, Kuwait, Lesotho, Lithuania, Macau, Oman, Qatar, Saudi Arabia and Taiwan.[231]
In October 2020, the Islamic Republic News Agency announced pending regulations that would require bitcoin miners in Iran to sell bitcoin to the Central Bank of Iran, and the central bank would use it for imports.[232] Iran, as of October 2020, had issued over 1,000 bitcoin mining licenses.[232] The Iranian government initially took a stance against cryptocurrency, but later changed it after seeing that digital currency could be used to circumvent sanctions.[233] The US Office of Foreign Assets Control listed two Iranians and their bitcoin addresses as part of its Specially Designated Nationals and Blocked Persons List for their role in the 2018 Atlanta cyberattack whose ransom was paid in bitcoin.
Regulatory warnings
The U.S. Commodity Futures Trading Commission has issued four "Customer Advisories" for bitcoin and related investments.[12] A July 2018 warning emphasized that trading in any cryptocurrency is often speculative, and there is a risk of theft from hacking, and fraud.[235] In May 2014 the U.S. Securities and Exchange Commission warned that investments involving bitcoin might have high rates of fraud, and that investors might be solicited on social media sites.[236] An earlier "Investor Alert" warned about the use of bitcoin in Ponzi schemes.
The European Banking Authority issued a warning in 2013 focusing on the lack of regulation of bitcoin, the chance that exchanges would be hacked, the volatility of bitcoin's price, and general fraud.[238] FINRA and the North American Securities Administrators Association have both issued investor alerts about bitcoin.
Price manipulation investigation
An official investigation into bitcoin traders was reported in May 2018.[241] The U.S. Justice Department launched an investigation into possible price manipulation, including the techniques of spoofing and wash trades.[242][243][244]
The U.S. federal investigation was prompted by concerns of possible manipulation during futures settlement dates. The final settlement price of CME bitcoin futures is determined by prices on four exchanges, Bitstamp, Coinbase, itBit and Kraken. Following the first delivery date in January 2018, the CME requested extensive detailed trading information but several of the exchanges refused to provide it and later provided only limited data. The Commodity Futures Trading Commission then subpoenaed the data from the exchanges.[245][246]
State and provincial securities regulators, coordinated through the North American Securities Administrators Association, are investigating "bitcoin scams" and ICOs in 40 jurisdictions.[247]
Academic research published in the Journal of Monetary Economics concluded that price manipulation occurred during the Mt Gox bitcoin theft and that the market remains vulnerable to manipulation.[248] The history of hacks, fraud and theft involving bitcoin dates back to at least 2011.[249]
Research by John M. Griffin and Amin Shams in 2018 suggests that trading associated with increases in the amount of the Tether cryptocurrency and associated trading at the Bitfinex exchange account for about half of the price increase in bitcoin in late 2017.[250][251]
J.L. van der Velde, CEO of both Bitfinex and Tether, denied the claims of price manipulation: "Bitfinex nor Tether is, or has ever, engaged in any sort of market or price manipulation. Tether issuances cannot be used to prop up the price of bitcoin or any other coin/token on Bitfinex."
Criticisms
The Bank for International Settlements summarized several criticisms of bitcoin in Chapter V of their 2018 annual report. The criticisms include the lack of stability in bitcoin's price, the high energy consumption, high and variable transactions costs, the poor security and fraud at cryptocurrency exchanges, vulnerability to debasement (from forking), and the influence of miners.
François R. Velde, Senior Economist at the Chicago Fed, described bitcoin as "an elegant solution to the problem of creating a digital currency".[256] David Andolfatto, Vice President at the Federal Reserve Bank of St. Louis, stated that bitcoin is a threat to the establishment, which he argues is a good thing for the Federal Reserve System and other central banks, because it prompts these institutions to operate sound policies.
Economic concerns
Bitcoin, along with other cryptocurrencies, has been described as an economic bubble by at least eight Nobel Memorial Prize in Economic Sciences laureates at various times, including Robert Shiller on 1 March 2014,[197] Joseph Stiglitz on 29 November 2017,[259] and Richard Thaler on 21 December 2017.[260][261] On 29 January 2018, a noted Keynesian economist Paul Krugman has described bitcoin as "a bubble wrapped in techno-mysticism inside a cocoon of libertarian ideology",[188] on 2 February 2018, professor Nouriel Roubini of New York University has called bitcoin the "mother of all bubbles",[262] and on 27 April 2018, a University of Chicago economist James Heckman has compared it to the 17th-century tulip mania.[261]
Journalists, economists, investors, and the central bank of Estonia have voiced concerns that bitcoin is a Ponzi scheme.[263][264][265][266] In April 2013, Eric Posner, a law professor at the University of Chicago, stated that "a real Ponzi scheme takes fraud; bitcoin, by contrast, seems more like a collective delusion."[267] A July 2014 report by the World Bank concluded that bitcoin was not a deliberate Ponzi scheme.[268]: 7 In June 2014, the Swiss Federal Council examined concerns that bitcoin might be a pyramid scheme, and concluded that "since in the case of bitcoin the typical promises of profits are lacking, it cannot be assumed that bitcoin is a pyramid scheme."
Bitcoin wealth is highly concentrated, with 0.01% holding 27% of in-circulation currency, as of 2021.
In January, 2022, the Central Bank of Russia proposed to ban "all cryptocurrency issuance and operations, stop banks from investing in cryptocurrencies, block exchanging crypto for traditional currency, and introduce legal liability for using crypto in purchases" citing systemic financial risk.
Energy consumption and carbon footprint
Bitcoin has been criticized for the amount of electricity consumed by mining.[272] On the other hand, several papers concluded that Bitcoin mining could promote renewable energy sources if used as an additional source of income.[273][274]
As of 2022, the Cambridge Centre for Alternative Finance (CCAF) estimates that bitcoin consumes 131 TWh annually, representing 0.29% of the world's energy production and ranking bitcoin mining between Ukraine and Egypt in terms of electricity consumption.[275][276]
Until 2021, according to the CCAF much of bitcoin mining was done in China.[277][278] Chinese miners used to rely on cheap coal power in Xinjiang[279][280] in late autumn, winter and spring, and then migrate to regions with overcapacities in low-cost hydropower, like Sichuan, between May and October. In June 2021 China banned Bitcoin mining[281] and Chinese miners moved to other countries such as the US and Kazakhstan.[282] In January 2022, Kosovo banned mining for 60 days to save electricity amid blackouts. Bitcoin mining is concentrated in the Serbian enclaves in Kosovo where Kosovo Serbs do not recognize Kosovo as an independent state and have consequently not paid for electricity for more than two decades.[283] The same month, Erik Thedéen [sv], vice-chair of the European Securities and Markets Authority, called for an EU ban on proof of work crypto-mining to favor the proof of stake model and fight climate change;[284] while the Russian central bank proposed to ban crypto mining due to perceived risks to the country's energy supply.[271] According to Bloomberg News and Meduza, the Federal Security Service convinced the Central Bank to ban cryptocurrencies in Russia, as they are used to finance the opposition and independent media.[285][286]
As of September 2021, according to the New York Times, Bitcoin's use of renewables range from 40% to 75%.[272] According to the Bitcoin Mining Council and based on a survey of 32% of the current global bitcoin network, 56% of bitcoin mining came from renewable resources in Q2 2021.[287]
The development of intermittent renewable energy sources, such as wind power and solar power, is challenging because they cause instability in the electrical grid. Several papers concluded that these renewable power stations could use the surplus energy to mine Bitcoin and thereby reduce curtailment, hedge electricity price risk, stabilize the grid, increase the profitability of renewable energy infrastructure, and therefore accelerate transition to sustainable energy and decrease Bitcoin's carbon footprint.
Concerns about bitcoin's environmental impact relate bitcoin's energy consumption to carbon emissions.[294][295] The difficulty of translating the energy consumption into carbon emissions lies in the decentralized nature of bitcoin impeding the localization of miners to examine the electricity mix used. The results of recent studies analyzing bitcoin's carbon footprint vary.[296][297][298][299] A 2018 study published in Nature Climate Change by Mora et al. claimed that bitcoin "could alone produce enough CO2 emissions to push warming above 2 °C within less than three decades."[298] However, three other studies also published in Nature Climate Change later dismissed this analysis on account of its poor methodology and false assumptions with one study concluding: "[T]he scenarios used by Mora et al are fundamentally flawed and should not be taken seriously by the public, researchers, or policymakers."[300][301][302] According to studies published in Joule and American Chemical Society in 2019, bitcoin's annual energy consumption results in annual carbon emission ranging from 17[303] to 22.9 MtCO2 which is comparable to the level of emissions of countries as Jordan and Sri Lanka or Kansas City.[299] George Kamiya, writing for the International Energy Agency, says that "predictions about bitcoin consuming the entire world's electricity" are sensational, but that the area "requires careful monitoring and rigorous analysis".[304] One study done by Michael Novogratz's Galaxy Digital claimed that Bitcoin mining used less energy than the traditional banking system.
Use in illegal transactions
The use of bitcoin by criminals has attracted the attention of financial regulators, legislative bodies, law enforcement, and the media.[306] According to a 2020 report produced by the United States Attorney General's Cyber-Digital Task Force illicit uses of cryptocurrency typically fall into three categories: "(1) financial transactions associated with the commission of crimes; (2) money laundering and the shielding of legitimate activity from tax, reporting, or other legal requirements; or (3) crimes, such as theft, directly implicating the cryptocurrency marketplace itself." The report concludes that "for cryptocurrency to realize its truly transformative potential, it is imperative that these risks be addressed" and that "the government has legal and regulatory tools available at its disposal to confront the threats posed by cryptocurrency's illicit uses".
Several news outlets have asserted that the popularity of bitcoins hinges on the ability to use them to purchase illegal goods.[194][309] Nobel-prize winning economist Joseph Stiglitz says that bitcoin's anonymity encourages money laundering and other crimes.[310][311] According to the UK 2020 national risk assessment—a comprehensive assessment of money laundering and terrorist financing risk in the UK—the risk of using cryptoassets such as Bitcoin for money laundering and terrorism financing is assessed as "medium" (from "low" in the previous 2017 report).[312] Legal scholars suggested that the money laundering opportunities may be more perceived than real.[313] Blockchain analysis company Chainalysis concluded that illicit activities like cybercrime, money laundering and terrorism financing made up only 0.15% of all crypto transactions conducted in 2021, representing a total of $14 billion.
Software implementation
Bitcoin Core is free and open-source software that serves as a bitcoin node (the set of which form the bitcoin network) and provides a bitcoin wallet which fully verifies payments. It is considered to be bitcoin's reference implementation.[317] Initially, the software was published by Satoshi Nakamoto under the name "Bitcoin", and later renamed to "Bitcoin Core" to distinguish it from the network.[318] It is also known as the Satoshi client.[319]
The MIT Digital Currency Initiative funds some of the development of Bitcoin Core.[320] The project also maintains the cryptography library libsecp256k1.[321]
Bitcoin Core includes a transaction verification engine and connects to the bitcoin network as a full node.[319] Moreover, a cryptocurrency wallet, which can be used to transfer funds, is included by default.[321] The wallet allows for the sending and receiving of bitcoins. It does not facilitate the buying or selling of bitcoin. It allows users to generate QR codes to receive payment.
The software validates the entire blockchain, which includes all bitcoin transactions ever. This distributed ledger which has reached more than 235 gigabytes in size as of Jan 2019, must be downloaded or synchronized before full participation of the client may occur.[319] Although the complete blockchain is not needed all at once since it is possible to run in pruning mode. A command line-based daemon with a JSON-RPC interface, bitcoind, is bundled with Bitcoin Core. It also provides access to testnet, a global testing environment that imitates the bitcoin main network using an alternative blockchain where valueless "test bitcoins" are used. Regtest or Regression Test Mode creates a private blockchain which is used as a local testing environment.[322] Finally, bitcoin-cli, a simple program which allows users to send RPC commands to bitcoind, is also included.
Checkpoints which have been hard coded into the client are used only to prevent Denial of Service attacks against nodes which are initially syncing the chain. For this reason the checkpoints included are only as of several years ago.[323][324][failed verification] A one megabyte block size limit was added in 2010 by Satoshi Nakamoto. This limited the maximum network capacity to about three transactions per second.[325] Since then, network capacity has been improved incrementally both through block size increases and improved wallet behavior. A network alert system was included by Satoshi Nakamoto as a way of informing users of important news regarding bitcoin.[326] In November 2016 it was retired. It had become obsolete as news on bitcoin is now widely disseminated.
Bitcoin Core includes a scripting language inspired by Forth that can define transactions and specify parameters.[327] ScriptPubKey is used to "lock" transactions based on a set of future conditions. scriptSig is used to meet these conditions or "unlock" a transaction. Operations on the data are performed by various OP_Codes. Two stacks are used - main and alt. Looping is forbidden.
Bitcoin Core uses OpenTimestamps to timestamp merge commits.[328]
The original creator of the bitcoin client has described their approach to the software's authorship as it being written first to prove to themselves that the concept of purely peer-to-peer electronic cash was valid and that a paper with solutions could be written. The lead developer is Wladimir J. van der Laan, who took over the role on 8 April 2014.[329] Gavin Andresen was the former lead maintainer for the software client. Andresen left the role of lead developer for bitcoin to work on the strategic development of its technology.[329] Bitcoin Core in 2015 was central to a dispute with Bitcoin XT, a competing client that sought to increase the blocksize.[330] Over a dozen different companies and industry groups fund the development of Bitcoin Core.
In popular culture
Term "HODL"
Hodl (/ˈhɒdəl/ HOD-əl; often written HODL) is slang in the cryptocurrency community for holding a cryptocurrency rather than selling it. A person who does this is known as a Hodler. It originated in a December 2013 post on the Bitcoin Forum message board by an apparently inebriated user who posted with a typo in the subject, "I AM HODLING."[331] It is often humorously suggested to be a backronym to "hold on for dear life".[332] In 2017, Quartz listed it as one of the essential slang terms in Bitcoin culture, and described it as a stance, "to stay invested in bitcoin and not to capitulate in the face of plunging prices."[333] TheStreet.com referred to it as the "favorite mantra" of Bitcoin holders.[334] Bloomberg News referred to it as a mantra for holders during market routs.[335]
Literature
In Charles Stross' 2013 science fiction novel, Neptune's Brood, the universal interstellar payment system is known as "bitcoin" and operates using cryptography.[336] Stross later blogged that the reference was intentional, saying "I wrote Neptune's Brood in 2011. Bitcoin was obscure back then, and I figured had just enough name recognition to be a useful term for an interstellar currency: it'd clue people in that it was a networked digital currency."
Film
The 2014 documentary The Rise and Rise of Bitcoin portrays the diversity of motives behind the use of bitcoin by interviewing people who use it. These include a computer programmer and a drug dealer.[338] The 2016 documentary Banking on Bitcoin is an introduction to the beginnings of bitcoin and the ideas behind cryptocurrency today.
Music
In 2018, a Japanese band called Kasotsuka Shojo – Virtual Currency Girls – launched. Each of the eight members represented a cryptocurrency, including Bitcoin, Ethereum and Cardano.
Academia
In September 2015, the establishment of the peer-reviewed academic journal Ledger (ISSN 2379-5980) was announced. It covers studies of cryptocurrencies and related technologies, and is published by the University of Pittsburgh.[342] The journal encourages authors to digitally sign a file hash of submitted papers, which will then be timestamped into the bitcoin blockchain. Authors are also asked to include a personal bitcoin address in the first page of their papers.
Non-fungible token
A non-fungible token (NFT) is a non-interchangeable unit of data stored on a blockchain, a form of digital ledger.[1] Types of NFT data units may be associated with digital files such as photos, videos, and audio. Because each token is uniquely identifiable, NFTs differ from blockchain cryptocurrencies, such as Bitcoin.
NFT ledgers claim to provide a public certificate of authenticity or proof of ownership, but the legal rights conveyed by an NFT can be uncertain. NFTs do not restrict the sharing or copying of the underlying digital files and do not prevent the creation of NFTs with identical associated files.
NFTs have been used as a speculative investment, and they have drawn criticism for the energy cost and carbon footprint associated with validating blockchain transactions as well as their frequent use in art scams.
Description
An NFT is a unit of data stored on a digital ledger, called a blockchain, which can be sold and traded.[3] The NFT can be associated with a particular digital or physical asset (such as a file or a physical object) and a license to use the asset for a specified purpose.[4] An NFT (and, if applicable, the associated license to use, copy or display the underlying asset) can be traded and sold on digital markets.[5] The extralegal nature of NFT trading usually results in an informal exchange of ownership over the asset that has no legal basis for enforcement,[6] often conferring little more than use as a status symbol.[7]
NFTs function like cryptographic tokens, but, unlike cryptocurrencies such as Bitcoin or Ethereum, NFTs are not mutually interchangeable, hence not fungible. While all bitcoins are equal, each NFT may represent a different underlying asset and thus may have a different value.[8] NFTs are created when blockchains string records of cryptographic hash, a set of characters identifying a set of data, onto previous records therefore creating a chain of identifiable data blocks.[9] This cryptographic transaction process ensures the authentication of each digital file by providing a digital signature that is used to track NFT ownership.[9] However, data links that point to details such as where the art is stored can be affected by link rot.[10]
Copyright
Ownership of an NFT does not inherently grant copyright or intellectual property rights to whatever digital asset the token represents.[11][12] While someone may sell an NFT representing their work, the buyer will not necessarily receive copyright privileges when ownership of the NFT is changed and so the original owner is allowed to create more NFTs of the same work.[13][14] In that sense, an NFT is merely a proof of ownership that is separate from a copyright.[12][15] According to legal scholar Rebecca Tushnet, "In one sense, the purchaser acquires whatever the art world thinks they have acquired. They definitely do not own the copyright to the underlying work unless it is explicitly transferred."[16] In practice, NFT purchasers do not generally acquire the copyright of the underlying artwork.
History
Early history (2014–2017)
The first known "NFT", Quantum,[18] was created by Kevin McCoy and Anil Dash in May 2014, consisting of a video clip made by McCoy's wife Jennifer. McCoy registered the video on the Namecoin blockchain and sold it to Dash for $4, during a live presentation for the Seven on Seven conference at the New Museum in New York City. McCoy and Dash referred to the technology as "monetized graphics".[19] A non-fungible, tradable blockchain marker was explicitly linked to a work of art, via on-chain metadata (enabled by Namecoin). This is in contrast to the multi-unit, fungible, metadata-less "colored coins" of other blockchains and Counterparty.[20]
In October 2015, the first NFT project, Etheria, was launched and demonstrated at DEVCON 1 in London, Ethereum's first developer conference, three months after the launch of the Ethereum blockchain. Most of Etheria's 457 purchasable and tradable hexagonal tiles went unsold for more than five years until March 13, 2021, when renewed interest in NFTs sparked a buying frenzy. Within 24 hours, all tiles of the current version and a prior version, each hardcoded to 1 ETH ($0.43 at the time of launch), were sold for a total of $1.4 million.[21]
The term "NFT" only gained currency with the ERC-721 standard, first proposed in 2017 via the Ethereum GitHub, following the launch of various NFT projects that year.[22][23] The standard coincided with the launch of several NFT projects, including Curio Cards, CryptoPunks (a project to trade unique cartoon characters, released by the American studio Larva Labs on the Ethereum blockchain)[24][25][26] and rare Pepe trading cards.
Increased public awareness (2017–present)
The 2017 online game CryptoKitties was monetized by selling tradable cat NFTs, and its success brought some public attention to NFTs.[27]
The NFT market experienced rapid growth during 2020, with its value tripling to $250 million.[28] In the first three months of 2021, more than $200 million were spent on NFTs.[29]
In the early months of 2021, interest in NFTs increased after a number of high-profile sales and art auctions.
Uses
Commonly associated files
NFTs have been used as a means of exchanging digital tokens that link to a digital file. Ownership of an NFT is often associated with a license to use the underlying digital asset, but generally does not confer copyright to the buyer. Some agreements only grant a license for personal, non-commercial use, while other licenses also allow commercial use of the underlying digital asset.
Digital art
Digital art is a common use case for NFTs.[32] High-profile auctions of digital art as NFTs have received considerable public attention, with the work "Merge" by artist Pak being the most expensive NFT with a a price of $91.8 million dollars[33] and Everydays: the First 5000 Days, by artist Mike Winkelmann (known professionally as Beeple), the second most expensive auction at US$69.3 million in 2021.[5][34]
Some NFT collections, including EtherRocks and CryptoPunks are examples of generative art, where many different images can be created by assembling a selection of simple picture components in different combinations.[35]
In March 2021, the blockchain company Injective Protocol bought a $95,000 original screen print entitled Morons (White) from English graffiti artist Banksy, and filmed somebody burning it with a cigarette lighter, with the video being minted and sold as an NFT.[36][37] The person who destroyed the artwork, who called themselves "Burnt Banksy", described the act as a way to transfer a physical work of art to the NFT space.
Games
NFTs can be used to represent in-game assets, such as digital plots of land, which some commentators describe as being controlled "by the user" instead of the game developer[39] by allowing assets to be traded on third-party marketplaces without permission from the game developer.[40]
CryptoKitties was an early successful blockchain online game where players adopt and trade virtual cats. The monetization of NFTs within the game raised a $12.5 million investment, with some kitties selling for over $100,000 each.[27][41][42] Following its success, CryptoKitties was added to the ERC-721 standard, which was created in January 2018 (and finalized in June).[43][22] A similar NFT-based online game, Axie Infinity, was launched in March 2018.
In October 2021, developer Valve banned applications that use blockchain technology or NFTs to exchange value or game artifacts from their Steam platform.[44]
In December 2021, Ubisoft announced Ubisoft Quartz, “an NFT initiative which allows people to buy artificially scarce digital items using cryptocurrency". The announcement has raised significant criticism, with 96% dislike ratio over the YouTube announcement video, which has since been unlisted.[45][46] Some Ubisoft developers have also raised their concern over the announcement.[47][48][49] The Game Developers Conference's 2022 annual report stated that 70 percent of developers surveyed said their studios had no interest in integrating NFTs or cryptocurrency into their games.
Music
In February 2021, NFTs reportedly generated around $25 million within the music industry, with artists selling artwork and music as NFT tokens.[51] On February 28, 2021, electronic dance musician 3LAU sold a collection of 33 NFTs for a total of $11.7 million to commemorate the three-year anniversary of his Ultraviolet album.[52][53] On March 3, 2021, an NFT was made to promote the Kings of Leon album When You See Yourself.[54][55][56] Other musicians that have used NFTs include American rapper Lil Pump,[57][58][59] Grimes,[60] visual artist Shepard Fairey in collaboration with record producer Mike Dean,[61] and rapper Eminem.
Film
In May 2018, 20th Century Fox partnered with Atom Tickets and released limited-edition Deadpool 2 digital posters to promote the film. They were available from OpenSea and the GFT exchange.[63][64] In March 2021 Adam Benzine's 2015 documentary Claude Lanzmann: Spectres of the Shoah became the first motion picture and documentary film to be auctioned as an NFT.[65]
Other projects in the film industry using NFTs include the announcement that an exclusive NFT artwork collection will be released for Godzilla vs. Kong[66] and director Kevin Smith announcing in April 2021 that his forthcoming horror movie Killroy Was Here would be released as an NFT.[67] The 2021 film Zero Contact, directed by Rick Dugdale and starring Anthony Hopkins, was also released as an NFT.[68][69]
In April 2021, an NFT associated with the score of the movie Triumph, composed by Gregg Leonard, was minted as the first NFT for a feature film score.[70]
In November 2021, film director Quentin Tarantino released seven NFTs based on uncut scenes of Pulp Fiction. Miramax subsequently filed a lawsuit claiming that their film rights were violated.
Fashion
Since 2021, fashion, apparel and luxury brands have ventured into the NFT space. In August 2021, Burberry announced that it had designed an exclusive collection of digital wearables for Blankos Block Party, a play-to-earn game developed by Mythical Games. The game also functions as a marketplace, where players can collect, sell and customize their “blankos” as NFTs.[72][73] In October 2021, Dolce & Gabbana made over US$6 million after auctioning off a nine-piece collection of fashion and couture NFTs.[74]
In November 2021, Morgan Stanley published a note suggesting that luxury-branded NFTs could become a US$56 billion market by 2030 and could see "dramatically" increased demand due to the metaverse.
Other associated files
A number of internet memes have been associated with NFTs, which were minted and sold by their creators or by their subjects.[76] Examples include Doge, an image of a Shiba Inu dog,[77] as well as Charlie Bit My Finger,[78] Nyan Cat[79][80] and Disaster Girl.[81]
Some virtual worlds, often marketed as metaverses, have incorporated NFTs as a means of trading virtual items and virtual real estate.[82]
Some pornographic works have been sold as NFTs, though hostility from NFT marketplaces towards pornographic material has presented significant drawbacks for creators.[83][84]
In May 2021, UC Berkeley announced that it would be auctioning NFTs for the patent disclosures for two Nobel Prize-winning inventions: CRISPR-Cas9 gene editing and cancer immunotherapy.[85] The university will continue to own the patents for these inventions, as the NFTs relate only to the university patent disclosure form, an internal form used by the university for researchers to disclose inventions.[85]
The first credited political protest NFT ("Destruction of Nazi Monument Symbolizing Contemporary Lithuania") was a video filmed by Professor Stanislovas Tomas on April 8, 2019, and minted on March 29, 2021. In the video, Tomas uses a sledgehammer to destroy a state-sponsored Lithuanian plaque located on the Lithuanian Academy of Sciences honoring Nazi war criminal Jonas Noreika.[86][87]
In early 2020, the developer of CryptoKitties, Dapper Labs, released the beta version of NBA TopShot, a project to sell tokenized collectibles of NBA highlights.[88] The project was built on top of Flow, a more efficient blockchain compared to Ethereum.[89] Later that year, the project was released to the public and reported over $230 million in gross sales as of February 28, 2021.
Speculation
NFTs representing certain digital collectables and artworks have seen considerable use as a speculative asset.[90] The NFT buying surge was called an economic bubble by experts, who also compared it to the Dot-com bubble.[91][92] In March 2021 Mike Winkelmann called NFTs an "irrational exuberance bubble".[93] By mid-April 2021, demand appeared to have substantially subsided, causing prices to fall significantly.
Money laundering
NFTs, as with other blockchain securities and traditional art sales, can potentially be utilized for money laundering.[95] Auction platforms for NFT sales may potentially face regulatory pressure for compliance with existing anti-money laundering legislation. Gou Wenjun, the director of the Anti-Money Laundering Monitoring and Analysis Centre for the People's Bank of China, has expressed that NFTs could “easily become money-laundering tools." Gou elaborated that there is an increasing unlawful exploitation of various new cryptographic technologies, and that illicit actors often self-identify as innovators of the financial technology sector.
Other uses
In 2019, Nike patented a system called CryptoKicks that would use NFTs to verify the authenticity of physical sneakers and give a virtual version of the shoe to the customer.[97]
Tickets, for any type of event, have been suggested for sale as NFTs.[98][99][100] Such proposals would enable event organizers or performers to garner royalties on resales.[101]
Some private online communities have been formed around the confirmed ownership of certain NFT releases.[102][103]
Standards in blockchains
Specific token standards have been created to support various blockchain use-cases. Ethereum was the first blockchain to support NFTs with its ERC-721 standard and is currently the most widely used. Many other blockchains have added or plan to add support for NFTs with their growing popularity.[104]
Ethereum
ERC-721[105] was the first standard for representing non-fungible digital assets on the Ethereum blockchain. ERC-721 is an inheritable Solidity smart contract standard, meaning that developers can create new ERC-721-compliant contracts by copying from a reference implementation. ERC-721 provides core methods that allow tracking the owner of a unique identifier, as well as a permissioned way for the owner to transfer the asset to others.[106]
The ERC-1155 standard offers "semi-fungibility", as well as providing an analogue to ERC-721 functionality (meaning that an ERC-721 asset could be built using ERC-1155). Unlike ERC-721 where a unique ID represents a single asset, the unique ID of an ERC-1155 token represent a class of assets, and there is an additional quantity field to represent the amount of the class that a particular wallet has.[107] The assets under the same class are interchangeable, and the user can transfer any amount of assets to others.[107]
Because Ethereum currently has high transaction fees (known as gas fees), layer 2 solutions for Ethereum have emerged which also supports NFTs:
- Immutable X – Immutable X is a layer 2 protocol for Ethereum designed specifically for NFTs, utilizing ZK rollups to eliminate gas fees for transactions.
- Polygon – Formerly known as the Matic Network, Polygon is a proof-of-stake blockchain which is supported by major NFT marketplaces such as OpenSea.
Other blockchains
- Bitcoin Cash – Bitcoin Cash supports NFTs and powers the Juungle NFT marketplace.
- Cardano – Cardano introduced native tokens that enable the creation of NFTs without smart contracts with its March 2021 update. Cardano NFT marketplaces include CNFT and Theos.
- Flow – The Flow blockchain, which uses a proof of stake consensus model, supports NFTs. CryptoKitties plans to switch from Ethereum to Flow in the future.
- GoChain – GoChain, a blockchain which bills itself as 'eco-friendly', powers the Zeromint NFT marketplace and the VeVe app.
- Solana – The Solana blockchain also supports non-fungible tokens.
- Tezos – Tezos is a blockchain network that operates on proof of stake and supports the sale of NFT art.
Issues and criticisms
Storage off-chain
NFTs involving digital art generally do not store the associated artwork file on the blockchain due to its size. The token functions in a way more similar to a certificate of ownership, with a web address pointing to the piece of art in question, making the art still subject to link rot.[19] Because NFTs are functionally separate from the underlying artworks, anybody can easily save a copy of an NFT's image, popularly through a right click. NFT supporters disparage this duplication of NFT artwork as a "right-clicker mentality", with one collector quoted by Vice comparing the value of a purchased NFT to that of a status symbol "to show off that they can afford to pay that much".[7]
The "right-clicker mentality" phrase spread virally after its introduction, particularly among those that were critical of the NFT marketplace who used the term to flaunt the ability to capture digital art backed by NFT with ease.[7] This criticism was promoted by Australian programmer Geoffrey Huntley who created "The NFT Bay", modeled after The Pirate Bay. The NFT Bay advertised a torrent file purported to contain 19 terabytes of digital art NFT images. Huntley compared his work to an art project from Pauline Pantsdown, and hoped the site would help educate users on what NFTs are and are not.[114]
Environmental concerns
NFT purchases and sales are enmeshed in a controversy regarding the high energy usage, and consequent greenhouse gas emissions, associated with blockchain transactions.[115] A major aspect of this is the proof-of-work protocol required to regulate and verify blockchain transactions on networks such as Ethereum, which consumes a large amount of electricity;[116][117] estimating the carbon footprint of a given NFT transaction involves a variety of assumptions about the manner in which that transaction is set up on the blockchain, the economic behavior of blockchain miners (and the energy demands of their mining equipment),[118] as well as the amount of renewable energy being used on these networks.[119] There are also conceptual questions, such as whether the carbon footprint estimate for an NFT purchase should incorporate some portion of the ongoing energy demand of the underlying network, or just the marginal impact of that particular purchase.[120] An analogy that's been described for this is the footprint associated with an additional passenger on a given airline flight.[115]>
Some more recent NFT technologies use alternative validation protocols, such as proof of stake, that have much less energy usage for a given validation cycle. Other approaches to reducing electricity include the use of off-chain transactions as part of minting an NFT.[115] A number of NFT art sites are also looking to address these concerns, and some are moving to using technologies and protocols with lower associated footprints.[121] Others now allow the option of buying carbon offsets when making NFT purchases, although the environmental benefits of this have been questioned.[122] In some instances, NFT artists have decided against selling some of their own work to limit carbon emission contributions.
Artist and buyer fees
Sales platforms charge artists and buyers fees for minting, listing, claiming and secondary sales. Analysis of NFT markets in March 2021, in the immediate aftermath of Beeple's "Everydays: the First 5000 Days" selling for US$69.3 million, found that most NFT artworks were selling for less than $200, with a third selling for less than $100.[124] Those selling below $100 were paying network usage fees between 72.5 and 157.5 per cent of that amount, meaning that such artists were on average paying more money in fees than they were making in sales.
Plagiarism and fraud
There have been cases of artists having their work sold by others as an NFT, without permission.[125] After the artist Qing Han died in 2020, her identity was assumed by a fraudster and a number of her works became available for purchase as NFTs.[126] Similarly, a seller posing as Banksy succeeded in selling an NFT supposedly made by the artist for $336,000 in 2021; with the seller in this case refunding the money after the case drew media attention.[127]
A process known as "sleepminting" can also allow a fraudster to mint an NFT in an artist's wallet and transfer it back to their own account without the artist becoming aware.[128] This allowed a white hat hacker to mint a fraudulent NFT that had seemingly originated from the wallet of the artist Beeple.[128]
The BBC reported a case of insider trading when an employee of the NFT marketplace OpenSea bought specific NFTs before they were launched, with the prior knowledge they would be promoted on the company's home page. NFT trading is an unregulated market that has no legal recourse for such abuses.[129]
In their announcement of developing NFT support for the graphics editor Photoshop, Adobe proposed creating an InterPlanetary File System database as an alternative means of establishing authenticity for digital works.[130]
The price paid for specific NFTs and sales volume of a particular author may be artificially inflated due to wash trading.
In popular culture
A comedy skit on the March 27, 2021 episode of Saturday Night Live featured characters explaining NFTs through rap to US Treasury Secretary Janet Yellen, as played by Kate McKinnon.[134]
The 2021 Paramount+ television film South Park: Post Covid: The Return of Covid featured an adult version of Butters Stotch in his Professor Chaos persona tricking people into purchasing NFTs in 2061. Although the film portrays them as a poor investment, he has grown so adept at selling them that he is locked in a mental institution.
Central bank digital currency
A central bank digital currency (CBDC) (also called digital fiat currency[1] or digital base money)[2] is a digital currency issued by a central bank, rather than by a commercial bank.
A report by the Bank for International Settlements states that, although the term "central bank digital currency" is not well-defined, "it is envisioned by most to be a new form of central bank money [...] that is different from balances in traditional reserve or settlement accounts."[3]
The present concept of CBDCs was inspired by Bitcoin and similar blockchain-based cryptocurrencies, but differs from such a virtual currency and cryptocurrency in that a CBDC is or would be issued by a state and have an official legal tender status.[3][4][5][6] Most CBDC implementations will likely not use or need any sort of distributed ledger such as a blockchain.[7][8]
CBDCs are presently mostly in the hypothetical stage, with some in proof-of-concept programmes; however, more than 80% of central banks are looking at digital currencies.[9][10] China's digital RMB was the first digital currency to be issued by a major economy.[11][12] On 27 September 2021, Tajikistan announced the creation of a CBDC with the Fantom Foundation, utilizing their Lachesis consensus aBFT technology. Nigeria was the first African country to launch its CBDC on 25 October 2021.
Central banks have directly implemented e-money previously, such as Finland's Avant stored value e-money card in the 1990s.[13] In 2000, the I LIKE Q [cs] in Czechia project was launched,[14][self-published source?] enabling the implementation of so-called micropayments on the Internet. For payments, users used the virtual currency Q, the fair value of which is tied to a fixed exchange rate against the Czech koruna in the ratio of 100 Q = CZK 1. The two currencies are fully convertible. The author of the project was Pepe Rafaj [cs]. Project I LIKE Q [cs] was terminated in 2003 due to an amendment to Czech law, which at that time did not provide for this form of payment. In 2021 the same group introduced project Corrency [cs] which is a type of digital currency enriched with smart contracts aka drone money.
The present concept of "central bank digital currency" may have been partially inspired by Bitcoin and similar blockchain-based cryptocurrencies. It is also a known concept in the field of economics, whereby the central bank enables citizens to hold accounts with it, providing a reliable and safe public savings or payments medium ("retail" or "general-purpose" CBDC).
The Bank for International Settlements (BIS) published a report in December 2020 listing the known CBDC wholesale and retail projects at that time.[15] By April 2021, there would be "at least 80 central banks around the world that are looking at digital currencies."[9]
Another 2020 BIS survey found that 86% of central banks were examining the advantages and disadvantages of launching CBDCs,[16] although only 14% were in advanced stages of development (such as pilots).
Implementation
A central bank digital currency would likely be implemented using a database run by the central bank, government, or approved private-sector entities.[7][8] The database would keep a record (with appropriate privacy and cryptographic protections) of the amount of money held by every entity, such as people and corporations.
In contrast to cryptocurrencies, a central bank digital currency would be centrally controlled (even if it was on a distributed database), and so a blockchain or other distributed ledger would likely not be required or useful - even as they were the original inspiration for the concept.[7][8]
Researchers propose multiple ways that a retail CBDC could be technologically implemented.[18]
Characteristics
CBDC is a high-security digital instrument; like paper bank notes, it is a means of payment, a unit of account, and a store of value.[19] And like paper currency, each unit is uniquely identifiable to prevent counterfeit.[20]
Digital fiat currency is part of the base money supply,[21] together with other forms of the currency. As such, DFC is a liability of the central bank just as physical currency is.[22] It is a digital bearer instrument that can be stored, transferred and transmitted by all kinds of digital payment systems and services. The validity of the digital fiat currency is independent of the digital payment systems storing and transferring the digital fiat currency.[23]
Proposals for CBDC implementation often involve the provision of universal bank accounts at the central banks for all citizens.
Benefits and impacts
Digital fiat currency is currently being studied and tested by governments and central banks in order to realize the many positive implications it contributes to financial inclusion, economic growth, technology innovation and increased transaction efficiencies.[26][27] Here is a list of potential advantages:
-
Technological efficiency: instead of relying on intermediaries such as banks and clearing houses, money transfers and payments could be made in real time, directly from the payer to the payee. Being real time has a couple of major advantages
- Reduces risk: payment for goods and services often needs to be done in a timely manner and when payment verification is slow, merchants usually accept the risk of some payments not succeeding in exchange for faster service to customers. When these risks are eliminated with instant payment verifications, merchants no longer need to use intermediaries to handle the risk or to absorb the risk cost themselves.
- Reduces complexity: merchants will not need to separately keep track of transactions that are slow (where the customer claims to have paid but the money has not arrived yet), therefore eliminate the waiting queue, which could simplify the transaction process from payment to rendition of goods/services.
- Reduces (or eliminates) transaction fees: current payment systems like Visa, Mastercard, American Express etc. have a fee attached to each transaction and lowering or eliminating these fees could lead to widespread price drops and increased adoption of digital payments.
- Financial inclusion: safe money accounts at the central banks could constitute a strong instrument of financial inclusion, allowing any legal resident or citizen to be provided with a free or low-cost basic bank account.
-
Preventing illicit activity: A CBDC makes it feasible for a central bank to keep track of the exact location of every unit of the currency (assuming the more probable centralized, database form); tracking can be extended to cash by requiring that the banknote serial numbers used in each transaction be reported to the central bank. This tracking has a couple of major advantages:
- Tax collection: It makes tax avoidance and tax evasion much more difficult, since it would become impossible to use methods such as offshore banking and unreported employment to hide financial activity from the central bank or government.
- Combating crime: It makes it much easier to spot criminal activity (by observing financial activity), and thus put an end to it.[28] Furthermore, in cases where criminal activity has already occurred, tracking makes it much harder to successfully launder money, and it would often be straightforward to instantly reverse a transaction and return money to the victim of the crime.
- Proof of transaction: a digital record exists to prove that money changed hands between two parties which avoids problems inherent to cash such as short-changing, cash theft and conflicting testimonies.
- Protection of money as a public utility: digital currencies issued by central banks would provide a modern alternative to physical cash – whose abolition is currently being envisaged.
- Safety of payments systems: A secure and standard interoperable digital payment instrument issued and governed by a Central Bank and used as the national digital payment instruments boosts confidence in privately controlled money systems and increases trust in the entire national payment system[30][31] while also boosting competition in payment systems.
- Preservation of seigniorage income: public digital currency issuance would avoid a predictable reduction of seigniorage income for governments in the event of a disappearance of physical cash.
- Banking competition: the provision of free bank accounts at the central bank offering complete safety of money deposits could strengthen competition between banks to attract bank deposits, for example by offering once again remunerated sight deposits.
- Monetary policy transmission: the issuance of central bank base money through transfers to the public could constitute a new channel for monetary policy transmission[33][34][35] (i.e. helicopter money[36]), which would allow more direct control of the money supply than indirect tools such as quantitative easing and interest rates, and possibly lead the way towards a full reserve banking system.[37] In digital Yuan trial in Shenzhen, the CBDC was programmed with an expiration date, which encouraged spending and discouraged money from sitting in a saving account. In the end, 90% of vouchers were spent in shops.
- Financial safety: CBDC would limit the practice of fractional reserve banking and potentially render deposit guarantee schemes less needed.
Risks
Despite having potential advantages, there are also risks associated with central bank digital currencies.
Data from tracing money routes can lead to surveillance,
Despite having potential advantages, there are also risks associated with central bank digital currencies.
-
Banking system disintermediation: With the ability to provide digital currency directly to its citizens, one concern is that depositors would shift out of the banking system.
Indeed, in the last century, commercial banks have created money thanks to deposits in addition to a number of other ways. Formally they have used 2 methods: fractional reserve banking and zero reserve.
Zero reserve: today commercial banks in some countries (US, UK, EU, etc) don't need a reserve requirement anymore [40][41] [42] [43] . Indeed every time a subject (a person, a corporation, etc) asks for a loan, and that subject offers a loan guarantee (a private property like a car, a building, etc), the bank temporarily creates a new deposit (money), lends this money to them, and when the borrower pays off the loan plus the interest the initial deposit is deleted, and the bank keeps the interest.
In the real world, zero reserve and fractional reserve are the same, because the banks are able to avoid the reserve requirements.
CBDCs are fully reserved, so if a person wants this form of money, they just buy it from the central bank. In this case commercial banks don't create debt or new money, and they don't earn any interest.
Customers may deem the safety, liquidity, solvibility, and publicity of CBDCs to be more attractive,[44] weakening the balance sheet position of commercial banks.[45] In the extreme, this could precipitate potential bank runs[46] and thus make banks' funding positions weaker. However, the Bank of England found that if the introduction of CBDC follows a set of core principles the risk of a system-wide run from bank deposits to CBDC is addressed.[47] A central bank could also limit the demand of CBDCs by setting a ceiling on the amount of holdings.[44] - Centralization: Since most central bank digital currencies are centralized, rather than decentralized like most cryptocurrencies, the controllers of the issuance of CBDC can add or remove money from anyone's account with a flip of a switch. In contrast, cryptocurrencies with a distributed ledger such as Bitcoin prevent this unless a group of users controlling more than 50% of mining power is in agreement.
- Digital dollarization: A well-run foreign digital currency could become a replacement for a local currency for the same reasons as those described in dollarization.[49] The announcement of Facebook's Libra contributed to the increased attention to CBDCs by central bankers,[50] as well as China's progress with DCEP to that of several Asian economies.
- Stalling social developments: Data from tracing money routes can lead to losing financial privacy. This can lead to encouraging of self-censorship, deterioration of freedom of expression and association, and ultimately to stalling social developments. For example, would the Cannabis revolution have happened if it was impossible to buy it with cash?
Decentralized finance
Decentralized finance (DeFi) offers financial instruments without relying on intermediaries such as brokerages, exchanges, or banks. Instead, it uses smart contracts on a blockchain. DeFi platforms allow people to lend or borrow funds from others, speculate on price movements on assets using derivatives, trade cryptocurrencies, insure against risks, and earn interest in savings-like accounts.[1] DeFi uses a layered architecture and highly composable building blocks.[2] Some applications promote high interest rates[1] but are subject to high risk.[3] As of October 2021, the value of assets used in decentralized finance amounted to $100 billion.
History
The Ethereum blockchain popularised smart contracts, which are the basis of DeFi, in 2017. Other blockchains have since implemented smart contracts, including Algorand, Cardano, EOS and Polkadot.
MakerDAO is a prominent lending DeFi platform based on a stablecoin that was established in 2017.[5] [6] It allows users to borrow Dai, a token pegged to the US dollar. Through a set of smart contracts that govern the loan, repayment, and liquidation processes, MakerDAO aims to maintain the stable value of Dai in a decentralized and autonomous manner.[7][8]
In June 2020, Compound Finance started rewarding lenders and borrowers of cryptocurrencies with, in addition to typical interest payments to lenders, units of a cryptocurrency called COMP. This token, which is used for running Compound, can also be traded on cryptocurrency exchanges. Other platforms followed suit, leading to "yield farming" or "liquidity mining," where speculators shift cryptocurrency assets between pools in a platform and between platforms to maximize their total yield, which includes not only interest and fees but also the value of additional tokens received as rewards.[9]
In July 2020, The Washington Post described decentralized finance techniques and the risks involved.[9] In September 2020, Bloomberg said that DeFi made up two-thirds of the cryptocurrency market in terms of price changes and that DeFi collateral levels had reached $9 billion.[10] Ethereum saw a rise in developers during 2020 due to the increased interest in DeFi.[11]
DeFi has attracted large cryptocurrency venture capitalists such as Andreessen Horowitz,[3] Tiger Global Management,[12] and Michael Novogratz.[13]
The Economist regarded the future of digital finance in 2022 as a "three-way fight" between: Big Tech, such as Facebook with its digital wallet; "big rich countries" that have been testing their own digital currencies; and software developers "building all sorts of applications" to decentralise finance. Handling the risks presented by crypto-assets already valued at $2.5 trillion was a particular challenge for US regulators.
Key characteristics
DeFi revolves around decentralized applications, also known as DApps, that perform financial functions on distributed ledgers called blockchains, a technology that was made popular by Bitcoin and has since been adapted more broadly.[15][1] Rather than transactions being made through a centralized intermediary such as a cryptocurrency exchange or a traditional securities exchange, transactions are directly made between participants, mediated by smart contract programs.[3] These smart contracts, or DeFi protocols, typically run using open-source software that is built and maintained by a community of developers.[16] The blockchain creators may provide specialised languages for writing smart contracts, such as Solidity for Ethereum, Hyperledger tools, and Plutus and Marlowe for Cardano. Otherwise they can be written in the blockchain's native language, such as Haskell for Cardano, and Rust, C, or C++ in Solana.
DApps are typically accessed through a browser extension or application. For example, MetaMask allows users to directly interact with Ethereum through a digital wallet.[17][18] Many of these DApps can be linked to create complex financial services.[1] For example, stablecoin holders can lend assets like USD Coin or Dai to a liquidity pool in a borrow/lending protocol like Aave, and allow others to borrow those digital assets by depositing their own collateral.[19] The protocol automatically adjusts interest rates based on the demand for the asset.[3] Some DApps source external (off-chain) data, such as the price of an asset, through blockchain oracles.[20]
Additionally, Aave introduced "flash loans", which are uncollateralized loans of an arbitrary amount that are taken out and provably paid back within a single blockchain transaction.[21] While there can be legitimate uses for flash loans such as arbitrage, collateral swap, self-liquidation, and unwinding leveraged positions, many exploits of DeFi platforms have used flash loans to manipulate cryptocurrency spot prices.[22]
Another DeFi protocol is Uniswap, which is a decentralized exchange (DEX) set up to trade tokens issued on Ethereum. Rather than using a centralized exchange to fill orders, Uniswap pays users to form liquidity pools in exchange for a percentage of the fees that traders earn by swapping tokens in and out of the liquidity pools. Because no centralized party runs Uniswap (the platform is governed by its users), and any development team can use the open-source software, there is no entity to check the identities of the people using the platform and meet KYC/AML regulations. It is not clear what position regulators will take on the legality of such platforms.
Errors and hacking
Coding errors and hacks are common in DeFi.[24][1] Blockchain transactions are irreversible, which means that an incorrect or fraudulent DeFi transaction cannot be corrected easily. For example, in 2020, a platform known as Yam Finance took deposits equivalent to $750 million within days of its launch before crashing because of a coding error. Additionally, the code for the smart contracts is generally open-source software that can be copied to set up competing platforms, which creates instabilities as funds shift from platform to platform.[16]
The person or entity behind a DeFi protocol may be unknown, and may disappear with investors' money.[16] Investor Michael Novogratz has described some DeFi protocols as "Ponzi-like".[13]
DeFi has been compared to the initial coin offering craze of 2017, part of a cryptocurrency bubble. Inexperienced investors are at particular risk of losing money because of the sophistication required to interact with DeFi platforms and the lack of any intermediary with customer support.[24][25]
In 2021, half of cryptocurrency crime was related to DeFi. This rise has been attributed to a combination of developer incompetence and non-existent or poorly enforced regulations.[26][27][28] Theft from DeFi can come from either external hackers stealing from vulnerable projects, or "rug pulls", where the developers and influencers promote a project and then take the money, as a form of pump-and-dump.
Cryptocurrency wallet
A cryptocurrency wallet is a device,[1] physical medium,[2] program or a service which stores the public and/or private keys[3] for cryptocurrency transactions. In addition to this basic function of storing the keys, a cryptocurrency wallet more often also offers the functionality of encrypting and/or signing information. Signing can for example result in executing a smart contract, a cryptocurrency transaction (see "bitcoin transaction" image), identification or legally signing a 'document' (see "application form" image).
Technology
Private and public key generation
A crypto currency wallet works by a theoretical or random number being generated and used with a length that depends on the algorithm size of the cryptocurrency's technology requirements. The number is then converted to a private key using the specific requirements of the cryptocurrency cryptography algorithm requirement. A public key is then generated from the private key using whichever cryptographic algorithm requirements are required. The private key is utilised by the owner to access and send cryptocurrency and is private to the owner, whereas the public key is to be shared to any third party to receive cryptocurrency.
Up to this stage no computer or electronic device is required and all key pairs can be mathematically derived and written down by hand. The private key and public key pair (known as an address) are not known by the blockchain or anyone else. The blockchain will only record the transaction of the public address when cryptocurrency is sent to it, thus recording in the blockchain ledger the transaction of the public address.
Duplicate private keys
Collision (two or more wallets having the same private key) is theoretically possible, since keys can be generated without being used for transactions, and are therefore offline until recorded in the blockchain ledger. However, this possibility is negated because the theoretical probability of two or more private keys being the same is extremely low. The number of possible wallets in any cryptocurrency cryptography is slightly less than the number of atoms in the universe[citation needed], a number so high that duplicating or hacking a certain key would be inconceivable.
Seed phrases
In modern convention a seed phrase is now utilised which is a 12 to 24 word and greater word phrase that is an unencrypted form of the private key in dictionary word format which is simpler to remember than an encrypted cryptographic key in another string format. When online, exchange and hardware wallets are generated using random numbers a seed phrase is asked to be recorded by the user, so that when access to the wallet becomes misplaced, damaged or compromised, the seed phrase can be used to re-access the wallet and associated keys and cryptocurrency.
Wallets
A number of technologies known as wallets exist that store the key value pair of private and public key known as wallets. A wallet hosts the details of the key pair making transacting cryptocurrency possible. Multiple methods exist for storing keys or seeds in a wallet.
Crypto wallets vis-à-vis dapp browsers
Dapp browsers are specialized software that sustains new generation decentralized applications. Dapp browsers are considered to be the browsers of Web3 and are the gateway to access the decentralized applications which are working based on blockchain technology. That means all dapp browsers must have a unique code system to unify all the different codes of the dapps.
While crypto wallets are focused on the exchange, purchase, sale of digital assets[9] and support narrowly targeted applications, the browsers support different kinds of applications of various formats, including exchange, games, NFTs marketplaces, etc.
Technical specifications of different browsers may or may not include features such as:
- Full support for all modern Web2.0 technologies;
- Built-in Ethereum mainnet/testnet RPC, fully compatible with Web3.0;
- Built-in Ethereum wallet (using smart contracts);
- Dapp naming support
Characteristics
In addition to the basic function of storing the keys, a cryptocurrency wallet may also have one or more of the following characteristics.
Simple cryptocurrency wallet
A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receive or spend cryptocurrencies.[11] A public key allows others to make payments to the address derived from it, whereas a private key enables the spending of cryptocurrency from that address.[12]
The cryptocurrency itself is not in the wallet. In the case of bitcoin and cryptocurrencies derived from it, the cryptocurrency is decentrally stored and maintained in a publicly available distributed ledger called the blockchain.[11]
eID wallet
Some wallets are specifically designed to be compatible with a framework. The European Union is creating an eIDAS compatible European Self-Sovereign Identity Framework (ESSIF) which runs on the European Blockchain Services Infrastructure (EBSI). The EBSI wallet is designed to (securely) provide information, an eID and to sign 'transactions'.[4]
Multisignature wallet
In contrast to simple cryptocurrency wallets requiring just one party to sign a transaction, multisignature wallets require multiple parties to sign a transaction.[13] Multisignature wallets are designed for increased security.
Smart contract
In the cryptocurrency space, smart contracts are digitally signed in the same way a cryptocurrency transaction is signed. The signing keys are held in a cryptocurrency wallet.
Key derivation
Sequential deterministic wallet
A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a cryptographic hash function, e.g. SHA-256 (seed + n), where n is an ASCII-coded number that starts from 1 and increments as additional keys are needed.
Armory deterministic wallet
Bitcoin Armory, an open source, Python-based, wallet-management application for the Bitcoin network, utilized its own implementation the hierarchical deterministic scheme and served as inspiration for the BIP32 standard.
Non-deterministic wallet
Bitcoin Armory, an open source, Python-based, wallet-management application for the Bitcoin network, utilized its own implementation the hierarchical deterministic scheme and served as inspiration for the BIP32 standard
Non-deterministic wallet
In a non-deterministic wallet, each key is randomly generated on its own accord, and they are not seeded from a common key. Therefore, any backups of the wallet must store each and every single private key used as an address, as well as a buffer of 100 or so future keys that may have already been given out as addresses but not received payments yet.
Wallet access permissions
When choosing a wallet, the owner must keep in mind who is supposed to have access to (a copy of) the private keys and thus potentially has signing capabilities. In case of cryptocurrency the user needs to trust the provider to keep the cryptocurrency safe, just like with a bank. Trust was misplaced in the case of the Mt. Gox exchange, which 'lost' most of their clients' bitcoins. Downloading a cryptocurrency wallet from a wallet provider to a computer or phone does not automatically mean that the owner is the only one who has a copy of the private keys. For example, with Coinbase, it is possible to install a wallet on a phone and to also have access to the same wallet through their website.
Vulnerabilities
A wallet can also have known or unknown vulnerabilities. A supply chain attack or side-channel attack are ways of a vulnerability introduction. In extreme cases even a computer which is not connected to any network can be hacked.
When using a software wallet for receiving cryptocurrency, access to the receiving wallet is not needed—the sending party only need know the destination address, thus anyone can send cryptocurrency to an address. Only the one who has the private key of the corresponding (public key) address otherwise has access.
Semantic Web
The Semantic Web (sometimes known as Web 3.0) is an extension of the World Wide Web through standards set by the World Wide Web Consortium (W3C).[1] The goal of the Semantic Web is to make Internet data machine-readable.
To enable the encoding of semantics with the data, technologies such as Resource Description Framework (RDF)[2] and Web Ontology Language (OWL)[3] are used. These technologies are used to formally represent metadata. For example, ontology can describe concepts, relationships between entities, and categories of things. These embedded semantics offer significant advantages such as reasoning over data and operating with heterogeneous data sources.[4]
These standards promote common data formats and exchange protocols on the Web, fundamentally the RDF. According to the W3C, "The Semantic Web provides a common framework that allows data to be shared and reused across application, enterprise, and community boundaries."[5] The Semantic Web is therefore regarded as an integrator across different content and information applications and systems.
The term was coined by Tim Berners-Lee for a web of data (or data web)[6] that can be processed by machines[7]—that is, one in which much of the meaning is machine-readable. While its critics have questioned its feasibility, proponents argue that applications in library and information science, industry, biology and human sciences research have already proven the validity of the original concept.[8]
Berners-Lee originally expressed his vision of the Semantic Web in 1999 as follows:
I have a dream for the Web [in which computers] become capable of analyzing all the data on the Web – the content, links, and transactions between people and computers. A "Semantic Web", which makes this possible, has yet to emerge, but when it does, the day-to-day mechanisms of trade, bureaucracy and our daily lives will be handled by machines talking to machines. The "intelligent agents" people have touted for ages will finally materialize.[9]
The 2001 Scientific American article by Berners-Lee, Hendler, and Lassila described an expected evolution of the existing Web to a Semantic Web.[10] In 2006, Berners-Lee and colleagues stated that: "This simple idea…remains largely unrealized".[11] In 2013, more than four million Web domains (out of roughly 250 million total) contained Semantic Web markup.[12]
Example
In the following example, the text "Paul Schuster was born in Dresden" on a website will be annotated, connecting a person with their place of birth. The following HTML fragment shows how a small graph is being described, in RDFa-syntax using a schema.org vocabulary and a Wikidata ID:
The example defines the following five triples (shown in Turtle syntax). Each triple represents one edge in the resulting graph: the first element of the triple (the subject) is the name of the node where the edge starts, the second element (the predicate) the type of the edge, and the last and third element (the object) either the name of the node where the edge ends or a literal value (e.g. a text, a number, etc.).
The triples result in the graph shown in the given figure.
One of the advantages of using Uniform Resource Identifiers (URIs) is that they can be dereferenced using the HTTP protocol. According to the so-called Linked Open Data principles, such a dereferenced URI should result in a document that offers further data about the given URI. In this example, all URIs, both for edges and nodes (e.g. http://schema.org/Person, http://schema.org/birthPlace, http://www.wikidata.org/entity/Q1731) can be dereferenced and will result in further RDF graphs, describing the URI, e.g. that Dresden is a city in Germany, or that a person, in the sense of that URI, can be fictional.
The second graph shows the previous example, but now enriched with a few of the triples from the documents that result from dereferencing https://schema.org/Person (green edge) and https://www.wikidata.org/entity/Q1731 (blue edges).
Additionally to the edges given in the involved documents explicitly, edges can be automatically inferred: the triple
from the original RDFa fragment and the triple
from the document at https://schema.org/Person (green edge in the figure) allow to infer the following triple, given OWL semantics (red dashed line in the second Figure):
Background
The concept of the semantic network model was formed in the early 1960s by researchers such as the cognitive scientist Allan M. Collins, linguist M. Ross Quillian and psychologist Elizabeth F. Loftus as a form to represent semantically structured knowledge. When applied in the context of the modern internet, it extends the network of hyperlinked human-readable web pages by inserting machine-readable metadata about pages and how they are related to each other. This enables automated agents to access the Web more intelligently and perform more tasks on behalf of users. The term "Semantic Web" was coined by Tim Berners-Lee,[7] the inventor of the World Wide Web and director of the World Wide Web Consortium ("W3C"), which oversees the development of proposed Semantic Web standards. He defines the Semantic Web as "a web of data that can be processed directly and indirectly by machines".
Many of the technologies proposed by the W3C already existed before they were positioned under the W3C umbrella. These are used in various contexts, particularly those dealing with information that encompasses a limited and defined domain, and where sharing data is a common necessity, such as scientific research or data exchange among businesses. In addition, other technologies with similar goals have emerged, such as microformats.
Limitations of HTML
Many files on a typical computer can also be loosely divided into human-readable documents and machine-readable data. Documents like mail messages, reports, and brochures are read by humans. Data, such as calendars, address books, playlists, and spreadsheets are presented using an application program that lets them be viewed, searched, and combined.
Currently, the World Wide Web is based mainly on documents written in Hypertext Markup Language (HTML), a markup convention that is used for coding a body of text interspersed with multimedia objects such as images and interactive forms. Metadata tags provide a method by which computers can categorize the content of web pages. In the examples below, the field names "keywords", "description" and "author" are assigned values such as "computing", and "cheap widgets for sale" and "John Doe".
Because of this metadata tagging and categorization, other computer systems that want to access and share this data can easily identify the relevant values.
With HTML and a tool to render it (perhaps web browser software, perhaps another user agent), one can create and present a page that lists items for sale. The HTML of this catalog page can make simple, document-level assertions such as "this document's title is 'Widget Superstore'", but there is no capability within the HTML itself to assert unambiguously that, for example, item number X586172 is an Acme Gizmo with a retail price of €199, or that it is a consumer product. Rather, HTML can only say that the span of text "X586172" is something that should be positioned near "Acme Gizmo" and "€199", etc. There is no way to say "this is a catalog" or even to establish that "Acme Gizmo" is a kind of title or that "€199" is a price. There is also no way to express that these pieces of information are bound together in describing a discrete item, distinct from other items perhaps listed on the page.
Semantic HTML refers to the traditional HTML practice of markup following intention, rather than specifying layout details directly. For example, the use of denoting "emphasis" rather than , which specifies italics. Layout details are left up to the browser, in combination with Cascading Style Sheets. But this practice falls short of specifying the semantics of objects such as items for sale or prices.
Microformats extend HTML syntax to create machine-readable semantic markup about objects including people, organizations, events and products.[13] Similar initiatives include RDFa, Microdata and Schema.org.
Semantic Web solutions
The Semantic Web takes the solution further. It involves publishing in languages specifically designed for data: Resource Description Framework (RDF), Web Ontology Language (OWL), and Extensible Markup Language (XML). HTML describes documents and the links between them. RDF, OWL, and XML, by contrast, can describe arbitrary things such as people, meetings, or airplane parts.
These technologies are combined in order to provide descriptions that supplement or replace the content of Web documents. Thus, content may manifest itself as descriptive data stored in Web-accessible databases,[14] or as markup within documents (particularly, in Extensible HTML (XHTML) interspersed with XML, or, more often, purely in XML, with layout or rendering cues stored separately). The machine-readable descriptions enable content managers to add meaning to the content, i.e., to describe the structure of the knowledge we have about that content. In this way, a machine can process knowledge itself, instead of text, using processes similar to human deductive reasoning and inference, thereby obtaining more meaningful results and helping computers to perform automated information gathering and research.
Tim Berners-Lee calls the resulting network of Linked Data the Giant Global Graph, in contrast to the HTML-based World Wide Web. Berners-Lee posits that if the past was document sharing, the future is data sharing. His answer to the question of "how" provides three points of instruction. One, a URL should point to the data. Two, anyone accessing the URL should get data back. Three, relationships in the data should point to additional URLs with data.
Web 3.0
Semantic Web
Tim Berners-Lee has described the Semantic Web as a component of Web 3.0.[15]
People keep asking what Web 3.0 is. I think maybe when you've got an overlay of scalable vector graphics – everything rippling and folding and looking misty – on Web 2.0 and access to a semantic Web integrated across a huge space of data, you'll have access to an unbelievable data resource …
— Tim Berners-Lee, 2006
"Semantic Web" is sometimes used as a synonym for "Web 3.0",[16] though the definition of each term varies.
Challenges
Some of the challenges for the Semantic Web include vastness, vagueness, uncertainty, inconsistency, and deceit. Automated reasoning systems will have to deal with all of these issues in order to deliver on the promise of the Semantic Web.
- Vastness: The World Wide Web contains many billions of pages. The SNOMED CT medical terminology ontology alone contains 370,000 class names, and existing technology has not yet been able to eliminate all semantically duplicated terms. Any automated reasoning system will have to deal with truly huge inputs.
- Vagueness: These are imprecise concepts like "young" or "tall". This arises from the vagueness of user queries, of concepts represented by content providers, of matching query terms to provider terms and of trying to combine different knowledge bases with overlapping but subtly different concepts. Fuzzy logic is the most common technique for dealing with vagueness.
- Uncertainty: These are precise concepts with uncertain values. For example, a patient might present a set of symptoms that correspond to a number of different distinct diagnoses each with a different probability. Probabilistic reasoning techniques are generally employed to address uncertainty.
- Inconsistency: These are logical contradictions that will inevitably arise during the development of large ontologies, and when ontologies from separate sources are combined. Deductive reasoning fails catastrophically when faced with inconsistency, because "anything follows from a contradiction". Defeasible reasoning and paraconsistent reasoning are two techniques that can be employed to deal with inconsistency.
- Deceit: This is when the producer of the information is intentionally misleading the consumer of the information. Cryptography techniques are currently utilized to alleviate this threat. By providing a means to determine the information's integrity, including that which relates to the identity of the entity that produced or published the information, however credibility issues still have to be addressed in cases of potential deceit.
This list of challenges is illustrative rather than exhaustive, and it focuses on the challenges to the "unifying logic" and "proof" layers of the Semantic Web. The World Wide Web Consortium (W3C) Incubator Group for Uncertainty Reasoning for the World Wide Web[17] (URW3-XG) final report lumps these problems together under the single heading of "uncertainty".[18] Many of the techniques mentioned here will require extensions to the Web Ontology Language (OWL) for example to annotate conditional probabilities. This is an area of active research.
Standards
Standardization for Semantic Web in the context of Web 3.0 is under the care of W3C.
Components
The term "Semantic Web" is often used more specifically to refer to the formats and technologies that enable it.[5] The collection, structuring and recovery of linked data are enabled by technologies that provide a formal description of concepts, terms, and relationships within a given knowledge domain. These technologies are specified as W3C standards and include:
- Resource Description Framework (RDF), a general method for describing information
- RDF Schema (RDFS)
- Simple Knowledge Organization System (SKOS)
- SPARQL, an RDF query language
- Notation3 (N3), designed with human readability in mind
- N-Triples, a format for storing and transmitting data
- Turtle (Terse RDF Triple Language)
- Web Ontology Language (OWL), a family of knowledge representation languages
- Rule Interchange Format (RIF), a framework of web rule language dialects supporting rule interchange on the Web
- JavaScript Object Notation for Linked Data (JSON-LD), a JSON-based method to describe data
- ActivityPub, a generic way for client and server to communicate with each other. This is used by the popular decentralized social network Mastodon.
The Semantic Web Stack illustrates the architecture of the Semantic Web. The functions and relationships of the components can be summarized as follows:
- XML provides an elemental syntax for content structure within documents, yet associates no semantics with the meaning of the content contained within. XML is not at present a necessary component of Semantic Web technologies in most cases, as alternative syntaxes exist, such as Turtle. Turtle is a de-facto standard, but has not been through a formal standardization process.
- XML Schema is a language for providing and restricting the structure and content of elements contained within XML documents.
- RDF is a simple language for expressing data models, which refer to objects ("web resources") and their relationships. An RDF-based model can be represented in a variety of syntaxes, e.g., RDF/XML, N3, Turtle, and RDFa. RDF is a fundamental standard of the Semantic Web.
- RDF Schema extends RDF and is a vocabulary for describing properties and classes of RDF-based resources, with semantics for generalized-hierarchies of such properties and classes.
- OWL adds more vocabulary for describing properties and classes: among others, relations between classes (e.g. disjointness), cardinality (e.g. "exactly one"), equality, richer typing of properties, characteristics of properties (e.g. symmetry), and enumerated classes.
- SPARQL is a protocol and query language for semantic web data sources.
- RIF is the W3C Rule Interchange Format. It's an XML language for expressing Web rules that computers can execute. RIF provides multiple versions, called dialects. It includes a RIF Basic Logic Dialect (RIF-BLD) and RIF Production Rules Dialect (RIF PRD).
Current state of standardization
Well-established standards:
- RDF
- RDFS
- Rule Interchange Format (RIF)
- SPARQL
- Unicode
- Uniform Resource Identifier
- Web Ontology Language (OWL)
- XML
Not yet fully realized:
- Unifying Logic and Proof layers
- Semantic Web Rule Language (SWRL)
Applications
The intent is to enhance the usability and usefulness of the Web and its interconnected resources by creating semantic web services, such as:
- Servers that expose existing data systems using the RDF and SPARQL standards. Many converters to RDF exist from different applications.[24] Relational databases are an important source. The semantic web server attaches to the existing system without affecting its operation.
- Documents "marked up" with semantic information (an extension of the HTML tags used in today's Web pages to supply information for Web search engines using web crawlers). This could be machine-understandable information about the human-understandable content of the document (such as the creator, title, description, etc.) or it could be purely metadata representing a set of facts (such as resources and services elsewhere on the site). Note that anything that can be identified with a Uniform Resource Identifier (URI) can be described, so the semantic web can reason about animals, people, places, ideas, etc. There are four semantic annotation formats that can be used in HTML documents; Microformat, RDFa, Microdata and JSON-LD.[25] Semantic markup is often generated automatically, rather than manually.
- Common metadata vocabularies (ontologies) and maps between vocabularies that allow document creators to know how to mark up their documents so that agents can use the information in the supplied metadata (so that Author in the sense of 'the Author of the page' won't be confused with Author in the sense of a book that is the subject of a book review).
- Automated agents to perform tasks for users of the semantic web using this data.
- Web-based services (often with agents of their own) to supply information specifically to agents, for example, a Trust service that an agent could ask if some online store has a history of poor service or spamming.
Such services could be useful to public search engines, or could be used for knowledge management within an organization. Business applications include:
- Facilitating the integration of information from mixed sources
- Dissolving ambiguities in corporate terminology
- Improving information retrieval thereby reducing information overload and increasing the refinement and precision of the data retrieved
- Identifying relevant information with respect to a given domain
- Providing decision making support
In a corporation, there is a closed group of users and the management is able to enforce company guidelines like the adoption of specific ontologies and use of semantic annotation. Compared to the public Semantic Web there are lesser requirements on scalability and the information circulating within a company can be more trusted in general; privacy is less of an issue outside of handling of customer data.
Skeptical reactions
Practical feasibility
Critics question the basic feasibility of a complete or even partial fulfillment of the Semantic Web, pointing out both difficulties in setting it up and a lack of general-purpose usefulness that prevents the required effort from being invested. In a 2003 paper, Marshall and Shipman point out the cognitive overhead inherent in formalizing knowledge, compared to the authoring of traditional web hypertext:[31]
While learning the basics of HTML is relatively straightforward, learning a knowledge representation language or tool requires the author to learn about the representation's methods of abstraction and their effect on reasoning. For example, understanding the class-instance relationship, or the superclass-subclass relationship, is more than understanding that one concept is a “type of” another concept. […] These abstractions are taught to computer scientists generally and knowledge engineers specifically but do not match the similar natural language meaning of being a "type of" something. Effective use of such a formal representation requires the author to become a skilled knowledge engineer in addition to any other skills required by the domain. […] Once one has learned a formal representation language, it is still often much more effort to express ideas in that representation than in a less formal representation […]. Indeed, this is a form of programming based on the declaration of semantic data and requires an understanding of how reasoning algorithms will interpret the authored structures.
According to Marshall and Shipman, the tacit and changing nature of much knowledge adds to the knowledge engineering problem, and limits the Semantic Web's applicability to specific domains. A further issue that they point out are domain- or organization-specific ways to express knowledge, which must be solved through community agreement rather than only technical means.[31] As it turns out, specialized communities and organizations for intra-company projects have tended to adopt semantic web technologies greater than peripheral and less-specialized communities.[32] The practical constraints toward adoption have appeared less challenging where domain and scope is more limited than that of the general public and the World-Wide Web.[32]
Finally, Marshall and Shipman see pragmatic problems in the idea of (Knowledge Navigator-style) intelligent agents working in the largely manually curated Semantic Web:[31]
In situations in which user needs are known and distributed information resources are well described, this approach can be highly effective; in situations that are not foreseen and that bring together an unanticipated array of information resources, the Google approach is more robust. Furthermore, the Semantic Web relies on inference chains that are more brittle; a missing element of the chain results in a failure to perform the desired action, while the human can supply missing pieces in a more Google-like approach. […] cost-benefit tradeoffs can work in favor of specially-created Semantic Web metadata directed at weaving together sensible well-structured domain-specific information resources; close attention to user/customer needs will drive these federations if they are to be successful.
Cory Doctorow's critique ("metacrap") is from the perspective of human behavior and personal preferences. For example, people may include spurious metadata into Web pages in an attempt to mislead Semantic Web engines that naively assume the metadata's veracity. This phenomenon was well known with metatags that fooled the Altavista ranking algorithm into elevating the ranking of certain Web pages: the Google indexing engine specifically looks for such attempts at manipulation. Peter Gärdenfors and Timo Honkela point out that logic-based semantic web technologies cover only a fraction of the relevant phenomena related to semantics.
Censorship and privacy
Enthusiasm about the semantic web could be tempered by concerns regarding censorship and privacy. For instance, text-analyzing techniques can now be easily bypassed by using other words, metaphors for instance, or by using images in place of words. An advanced implementation of the semantic web would make it much easier for governments to control the viewing and creation of online information, as this information would be much easier for an automated content-blocking machine to understand. In addition, the issue has also been raised that, with the use of FOAF files and geolocation meta-data, there would be very little anonymity associated with the authorship of articles on things such as a personal blog. Some of these concerns were addressed in the "Policy Aware Web" project[35] and is an active research and development topic.
Doubling output formats
Another criticism of the semantic web is that it would be much more time-consuming to create and publish content because there would need to be two formats for one piece of data: one for human viewing and one for machines. However, many web applications in development are addressing this issue by creating a machine-readable format upon the publishing of data or the request of a machine for such data. The development of microformats has been one reaction to this kind of criticism. Another argument in defense of the feasibility of semantic web is the likely falling price of human intelligence tasks in digital labor markets, such as Amazon's Mechanical Turk.[citation needed]
Specifications such as eRDF and RDFa allow arbitrary RDF data to be embedded in HTML pages. The GRDDL (Gleaning Resource Descriptions from Dialects of Language) mechanism allows existing material (including microformats) to be automatically interpreted as RDF, so publishers only need to use a single format, such as HTML.
Research activities on corporate applications
The first research group explicitly focusing on the Corporate Semantic Web was the ACACIA team at INRIA-Sophia-Antipolis, founded in 2002. Results of their work include the RDF(S) based Corese[36] search engine, and the application of semantic web technology in the realm of distributed artificial intelligence for knowledge management (e.g. ontologies and multi-agent systems for corporate semantic Web) [37] and E-learning.[38]
Since 2008, the Corporate Semantic Web research group, located at the Free University of Berlin, focuses on building blocks: Corporate Semantic Search, Corporate Semantic Collaboration, and Corporate Ontology Engineering.[39]
Ontology engineering research includes the question of how to involve non-expert users in creating ontologies and semantically annotated content[40] and for extracting explicit knowledge from the interaction of users within enterprises.
Future of applications
Tim O'Reilly, who coined the term Web 2.0, proposed a long-term vision of the Semantic Web as a web of data, where sophisticated applications manipulate the data web.[41] The data web transforms the World Wide Web from a distributed file system into a distributed database system.
 Web3News
Web3News